A trojan horse has used the Tor anonymity network to communicate with command and control servers, researchers found.

The Tor communication capability was an addon function to the Bifrost backdoor trojan that allowed the malware to send stolen user data over the encrypted proxy network.
It was believed to be the first instance of malware using Tor, and while development of the Trojan appears to have stopped, researchers say use of the anonymised network was a useful concept.
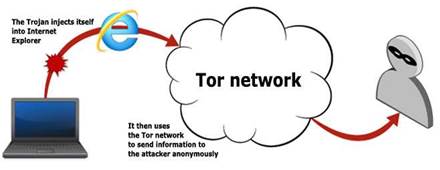
The Bifrost trojan targeted all Windows operating systems. It established links to command and control servers, once it had infected a host, by launching the Internet Explorer web browser and injecting into its address space.
Compromised machines then remained under the control of remote attackers over the Tor connection.
It specifically used Tor's server-side location-hidden services function that removed the risk of eavesdropping on the network's exit nodes.
Hidden services were hosted on user computers and used internal pseudodomains that could only be routed within the Tor network.
Bifrost's use of Tor to route traffic was a "novel idea", Symantec security response engineer Cathal Mullaney said.
It "adds an extra layer of stealth and security to the trojan," Mullaney said.
"This type of behavior is very useful from a trojan’s perspective as it provides a secure communication method while keeping the remote server anonymous."
Stolen data traversing was further protected by multi-layer encryption used in the Tor network.
"This increases the difficulty of analysing the communications between the compromised computer and the remote server."
Use of Tor also hindered attempts to block Bifrost connections at firewall level because, Mullaney said, it does not use "unusual" remote ports.


_(33).jpg&h=140&w=231&c=1&s=0)







 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



