Victims of the BadRabbit ransomware may be able to recover their scrambled files in certain circumstances thanks to coding mistakes made by the malware's authors.
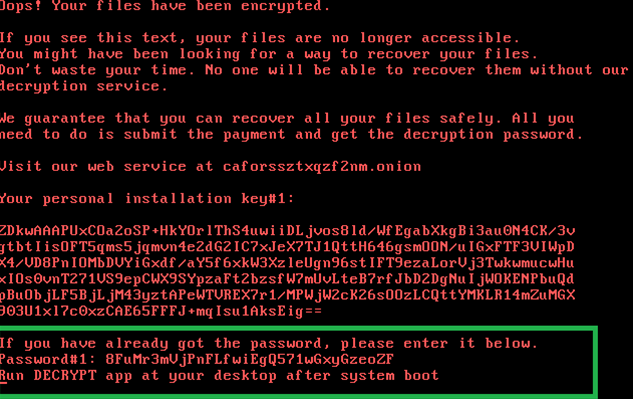
Security vendor Kaspersky Lab discovered that BadRabbit does not delete the password it generates when it encrypts victims' hard disks and files from the computer's memory.
"... there is a slim chance to extract it before the dispci.exe [encryption] process terminates," Kaspersky's researchers wrote.
However, if the system is rebooted, the key in memory will be erased. Without the 2048-bit key, there's no way to decrypt the scrambled data.
Additionally, BadRabbit doesn't attempt to delete the Windows Shadow Copy back-up files, the firm found.
If Shadow Copies are enabled prior to the BadRabbit strike, they can be used to restore original versions of the encrypted files through Windows or through third-party utilities.
BadRabbit and NotPetya one and the same
Further analysis of the malware by Cisco's Talos security researchers has found BadRabbit uses the EternalRomance exploit in a similar fashion to the NotPetya worm.
EternalRomance is one of several exploits leaked by the ShadowBrokers group of hackers that belonged to an organisation linked to the US National Security Agency.
The exploit targets vulnerable versions of Microsoft's Server Message Block (SMB) file sharing protocol, and is used by BadRabbit and NotPetya to move laterally across networked Windows systems.
Talos said the EternalRomance implementation for BadRabbit is similar to the Python-language implementation used by NotPetya.
The key difference between EternalRomance in BadRabbit and NotPetya is in BadRabbit the exploit is used to overwrite the kernel session security context in order to launch remote services.
In NotPetya, EternalRomance was used to install the DoublePulsar backdoor, an NSA-linked exploit also leaked by ShadowBrokers.
Talos said it was confident that BadRabbit had been built using the same code base as NotPetya. It also said both malware strains used a similar tool chain for assembly.


_(22).jpg&h=140&w=231&c=1&s=0)


_(20).jpg&h=140&w=231&c=1&s=0)



_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition












_(1).jpg&h=140&w=231&c=1&s=0)



