The macOS client application for the popular audio and video conferencing service Zoom can be made to forcibly join users to calls, activating Mac microphones video cameras without users being asked for permission, a researcher has found.
Security researcher Jonathan Leitschuh from software development automation company Gradle was curious how sending a simple meeting link would start up users' Zoom clients, simply by clicking on it so that the web browser would open it.
Leitschuh thought it was an "amazing bit of functionality" and wondered how it had been implemented securely by Zoom.
His curiosity led to the discovery of two serious vulnerabilities that are very simple to exploit, and which Leitschuh said exposes up to 750,000 companies around the world with over four million webcams being activated by malicious websites.
On top of being able to activate Mac webcams which Leitschuh wrote [Caution: link will join those who click on it to a call with the video camera activated] a proof of concept for , he said it's possible to launch denial of service attacks if a webpage repeatedly joins users to invalid calls.
Anyone who's installed the Zoom client and then uninstalled it will have a web server running on their machines listening on the localhost port.
This server will "happily reinstall the Zoom client for you, without requiring any user interaction on your behalf besides visiting a webpage."
Leitschuh said it appears that Zoom is abusing a hack to bypass cross-origin resource sharing protections.
How to avoid being Zoomed
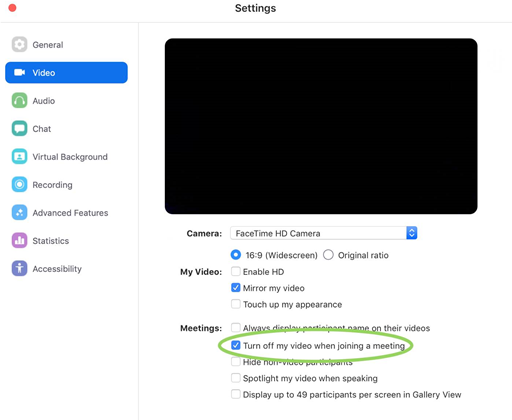
Although Leitschuh noted that Zoom did not fully fix the vulnerabilities within the 90-day industry standard disclosure period, users can can stop the client from turning on the webcam automatically if they're being joined to calls.
Going to the Settings dialog in the Zoom client, and then picking Video | Meetings | and ticking the Turn off my video when joining a meeting will see to this.
Running the UNIX list of open files command: lsof -i :19421 will reveal if the webserver bound to localhost is running, and provide its process identity number (PID).
With the process numbrer in hand, issue kill -9 [PID] and delete the ~/.zoomus directory to remove the web server application files, Leitschuh advised.
However, Leitschuh said that Zoom still has not fixed the forcible joining of users to call features, or the webserver re-installing uninstalled clients if webpages ask them to flaw.
The security researcher first contacted Zoom via email on March 26, and the company provided a quick fix solution.
Leitschuh was offered a bug bounty for his report the next day, which he declined as Zoom's policy is to require non-reporting of the vulnerability even after it's been patched.



_(28).jpg&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



