Microsoft claims a bug found in its memory address space layout randomisation (ASLR) security feature is an intended feature and not a flaw.
ASLR mitigates against attacks using techniques such as return-oriented programming (ROP) that rely on code being found in predictable or discoverable locations in system memory.
The security feature was introduced with Windows Vista, and loads executables that are explicitly compatible with ASLR in non-predictable address locations, making code re-use attacks difficult.
But the US CERT issued a vulnerability note last week, saying that Windows 8 and later "fail to properly randomise every application if system-wide mandatory ASLR is enabled via EMET [Microsoft's enhanced mitigation experience toolkit] or Windows Defender Exploit Guard".
However, Microsoft has denied the issue is a vulnerability, labelling it a "configuration issue" in WDEG that "does not create additional risk, and does not weaken the existing security posture of applications".
"ASLR is working as intended and the configuration issue described by CERT only affects applications where the EXE does not already opt-in to ASLR," Microsoft said.
The configuration issue identified by CERT prevents system-wide enablement of bottom-up randomisation - an additional ASLR feature that makes it even harder to guess or to discover where in a computer's memory code is loaded.
The feature adds entropy to the base address selected for memory allocations that search for a free region, starting from the bottom of the address space.
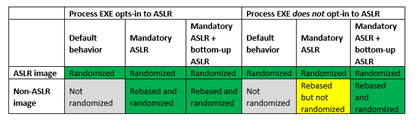
But bottom-up randomisation is not automatically enabled for processes when their executables do not opt in to ASLR, as shown in yellow in the table below. The table - published by Microsoft - explains the behaviour of ASLR in different configurations for processes:
"This means that bottom-up randomisation must also be enabled for entropy to be applied to images that are rebased by mandatory ASLR," Microsoft said.
"In practice, this issue only affects scenarios where an administrator is intentionally attempting to enable mandatory ASLR for a process that would otherwise not fully benefit from ASLR."
Microsoft said it was investigating and would address the issue.
It said as a manual workaround, administrators can edit the Windows Registry system configuration database to add a system-wide value.
It is also possible to enable mandatory ASLR and bottom-up randomisation on a per-program basis with WDEG or EMET, Microsoft said.




_(33).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



