Facebook founder Mark Zuckerberg has again been targeted by security researchers hoping to score cash by disclosing bugs to the social networking site's security service.

The social networking boss was used as a test dummy when a standard headshot of Zuckerberg within his account was used by a researcher to demonstrate a photo-erasing bug.
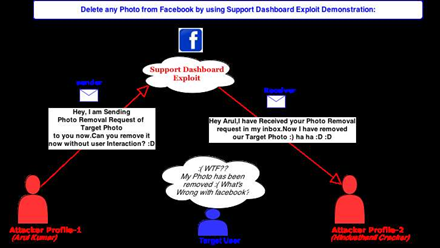
Arul Kumar sent a bug report to the Facebook security team detailing a hole that allowed anyone to delete photos from accounts across the social network. It worked by abusing a support service designed to allow users to request a photo be removed.
After the Facebook team rejected the validity of the bug, Kumar took to the camera to film a proof-of-concept video demonstrating twice how a photo in Zuckerberg's account could be erased.
Crucially, the researcher did not exploit the bug on Zuckerberg's account, stopping before submitting the photo removal request and therefore ensuring he did not breach the site's terms of service which would void his bid to gain the bug bounty.
Kumar instead then exploited the bug on photos within two dummy accounts.
The flaw was fixed and Kumar paid $12,500 under Facebook's bug bounty.
"We need two Facebook accounts to delete anyone's photo permanently,"Kumar wrote in a blog.
One account will act as 'sender' to send [a] claim message. Another account will act as 'receiver' who receives [a] photo removal link from [the] sender."
Facebook security staffer using the name Emrakul praised Kumar for the video and said he wished other bug reports were as detailed.
The bug required a manipulation of two URL text fields. This allowed takedown approval requests destined to Facebook support or the account holder of the photo in question to be redirected to anyone, including an attacker. It could also allow any photo to be taken down by swapping out the respective identifier.
Kumar's report comes after Zukerberg's account was last month targeted by a researcher who exploited a bug to post a status update on the Facebook founder's account.
Facebook patched the bug reported by researcher Khalil Shreateh but staunchly refused to pay him as he breached the site's terms of service by exploiting a legitimate Facebook user account.
While a bug bounty was raised in his behalf by internet users, many in the security community stood behind Facebook's decision saying an exception to the rules could at best set a bad precedent and at worst cause legal issues for the site.


_(23).jpg&h=140&w=231&c=1&s=0)

_(20).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



