A cross-platform trojan has been discovered that hijacks Windows and Mac OS X machines and mobile devices, and steals audio and video feeds, screenshots and keystrokes .

The comprehensive espionage toolkit dubbed BackDoor.DaVinci.1 malware was thought to be the first use of a rootkit to hide a trojan on the Apple operating system.
It allowed criminals to siphon data stolen by keyloggers to remote servers, along with screenshots, intercepted e-mail, and instant messaging chats including ICQ and Skype. Microphone and web cam feeds could also be captured.
DaVinci.1 also contained counter anti-virus and firewall tools.
Russian anti-virus vendor Dr Web discovered the malware after a user this week reported the infected image.
"The trojan poses a serious threat to users because it not only intercepts any information on the infected computer but also gives criminals full control over a compromised system so that they can render it non-operational," the company said.
It said the malware had "functional modules" that includes a backdoor component that is encrypted and uses rootkits.
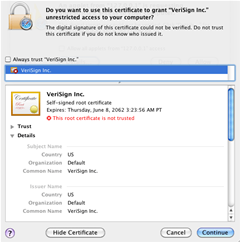
The malware spread via an Adobe Flash Player (*.jar) file that was signed with an invalid certificate.
DaVinci.1 would first detect the operating system of a target machine before launching malicious payloads.
Dr Web did not say which mobile operating platforms were also affected.

_(37).jpg&h=140&w=231&c=1&s=0)
_(36).jpg&h=140&w=231&c=1&s=0)







 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



