Social engineering remains the greatest security threat to Australian government agencies, according to the 2014 Australian Government Information Security Manual (ISM), which was published this week.
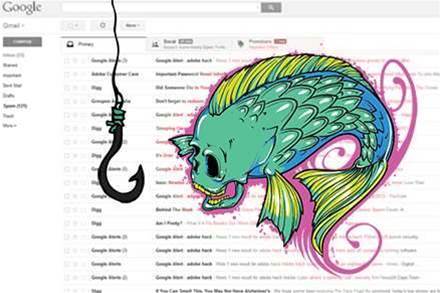
The manual highlights the increasing sophistication and highly targeted nature of attacks that are often realised in the form of an email sent by someone known to, and trusted by, the target.
“These campaigns are becoming increasingly tailored and credible ... some target a specific personal interest or a subject matter relevant to their work,” said the report.
The malicious emails usually contain links to fake websites that “can masquerade as a legitimate site used by an individual in order to mislead them into revealing personal information.”
Although this type of attack is nothing new -- the term spear phishing has been rattling around for years -- the problem is that the attacks have become more common and are extremely difficult to defend against.
When an attack is widespread, it becomes easier to discover and defend against, according to Gerry Tucker, managing director of Websense.
“When we look at advanced malware attacks, we see less of them in total but we see more of the very, very well targeted, well engineered attacks at individuals. This is very much spear phishing with laser-like focus,” he said.
Social media is to blame, said Wayne O’Young, an engineer at security firm Imperva.
“An easy tool to use is called LinkedIn," he said. "For example, if [an attacker] wants to gain access to an organisations’ database, maybe they could identify the company DBA (Database Administrator) through sites such as LinkedIn. With this information, they could create a very targeted attack,” he said.
The attacks don’t rely solely on email, said Ty Miller, founder of pen-testing firm Threat Intelligence. For example, in a recent penetration test at one of Miller’s clients, he was challenged with convincing an employee to insert a USB key into a PC connected to the corporate network.
“I went to the receptionist and told her I had a meeting with someone but had forgotten their name. However, I had a document with their name on this USB key and would they mind inserting it into their computer and opening it,” Miller said.
Unsurprisingly, the receptionist did insert the key and double clicked on the ‘malware’ about ten times.
“There was no suspicion around it because they couldn’t open the document and I just said, don’t worry about it, give me my USB key back, it’s probably damaged,” he said.
Miller likened the security challenge faced by all organisations to the old saying, “If you are being chased by a bear, you only need to be faster than the slowest runner.”
“The more security you put in place, the harder you are making it to get in. The harder you make it to get in, the more likely ‘they’ are going to move on to another easier target -- unless they specifically want you,” Miller said.
“If it is a state sponsored attack and they really want you, you can almost guarantee they will get in at some point,” he added.



_(37).jpg&h=140&w=231&c=1&s=0)
_(36).jpg&h=140&w=231&c=1&s=0)






 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



