A cross-site scripting (XSS) vulnerability in a Salesforce subdomain allowed attackers to gather end-user credentials through trusted applications from the cloud company, researchers at infosec firm Elastica have revealed.
Elastica researchers published details of the vulnerability over the weekend, having discovered the flaw and reported it to Salesforce in July.
They made the vulnerability public after Salesforce patched the hole last week.
The XSS vulnerability lived within the admin.salesforce.com subdomain, which the cloud company uses for blogging purposes.
It arose because a specific function in the deployed application failed to sanitise and filter arbitrary input passed to it by remote users as a part of an HTTP request, Elastica wrote.
Attackers could therefore inject arbitrary scripts from third-party domains and execute it on users' browsers when they visited the affected Salesforce subdomain.
Elastica said the vulnerability could easily be used to trick users into thinking a phishing email was legitimate because the message originated from the admin.salesforce.com host.
Similarly, its origination meant filters would not identify the email as being malicious.
Attackers could also use the vulnerability to execute JavaScript to steal cookies and session identifiers, leading to a potential account takeover. Additionally, they could force users to download malicious code on their machines by executing unauthorised scripts if a browser runs a vulnerable application.
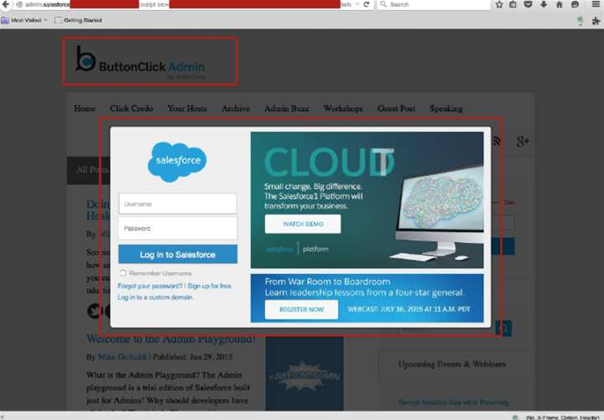
To demonstrate the attack, Elastica created a fake Salesforce login popup and injected it through a control point.
Users could be tricked through a well-crafted phishing attack to open the URL embedded in the phishing email, which would execute the malicious script and trigger the Salesforce login popup, Elastica demonstrated.
Despite the seriousness of the flaw, Salesforce took its time to patch the vulnerability because it considered it to be "low-threat" since it existed in the subdomain and not the main Salesforce website.
All Salesforce accounts for different applications were at risk because the company uses single sign on to manage multiple accounts, Elastica said.
"This XSS vulnerability could be dangerous if exploited. In this case study, the vulnerability was not present in “login.salesforce.com” but in another subdomain of Salesforce," the firm wrote.
"However, since the primary domain is “salesforce.com”, this trust can be exploited through phishing attacks by tricking users into providing their legitimate credentials. With [single sign on] accounts, the threat extends to all the accounts including accounts used for cloud applications."


_(36).jpg&h=140&w=231&c=1&s=0)
_(37).jpg&h=140&w=231&c=1&s=0)







 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



