Researchers warn that the actors behind the destructive Petya/NotPetya/GoldenEye malware campaign in Ukraine could return via a new vector.
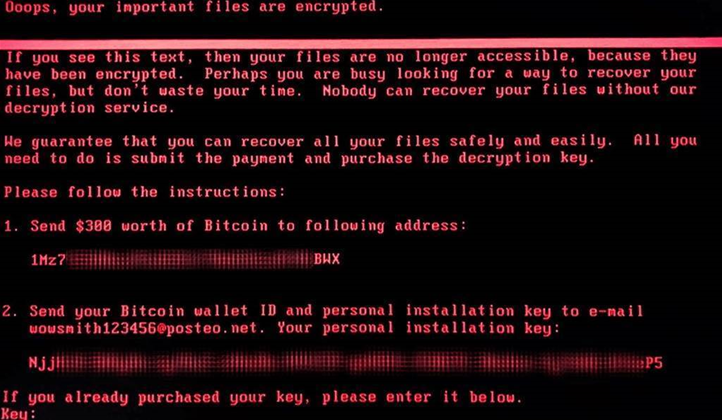
Using telemetry data, Cisco's Talos security offshoot has analysed how the Ukrainian MEDoc tax accounting firm's software update mechanism was compromised to deliver the malware.
Based on the recent spate of attacks, Talos believes the attackers could return through some other attack vector.
"In short, the actor has given up the ability to deliver arbitrary code to the 80 percent of UA businesses that use MEDoc as their accounting software, along with any multinational corporations that leveraged the software," the researchers wrote.
"This is a significant loss in operational capability, and ... it is unlikely that they would have expended this capability without confidence that they now have or can easily obtain similar capability in target networks of highest priority to the threat actor."
Talos urged organisations with ties to Ukraine to take extra caution, including applying software patches, moving to Windows 10, and deploying network intrusion detection and prevention systems immediately if they have branches in Ukraine.
The attackers compromised the MEDoc servers in April this year, using stolen credentials belonging to an administrator of the tax accounting software company.
With administrator access to much of MEDoc's networked systems, the attackers were able to release at least three software updates containing backdoors.
Earlier analysis by security vendor ESET discovered code inserted to a dynamic link library in the updates that allowed attackers to spy on targets, and download and run code remotely on their computer systems.
Police in Ukraine have seized servers at MEDoc, and the country has also extended its tax return filing deadline to help businesses hit by the supply chain attack.



_(33).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



