Attack research has been given a boost with the development of the first platform to help analyse exploits in a Java and a host of file types.

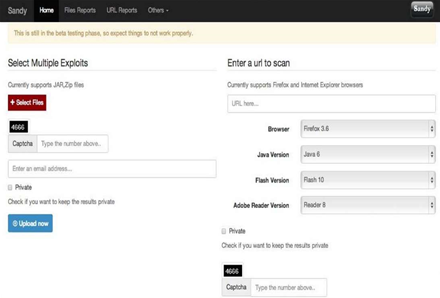
The tool dubbed Sandy was designed for static and dynamic analysis of formats including Microsoft Office .pdf, jar, Flash and HTML. The beta online version processes only Java exploits.
Security researcher Rahul Sasi (@fb1h2s) designed Sandy as a means to bulk process some of the 2000 exploits that emerged each day.

"... there are no sandboxes that process Java exploits at all. So their needs to be an intelligent specialised system that process these exploit samples," Sasi said.
"The main aim of Sandy is to extract the embedded executable, drop documents and URL controllers from file formats and provide attribution [of] attack groups and their technology."
He hoped organisations hit in targetd attacks would submit exploits to the free service to help build intelligence sharing and shore up broader security postures.
Sandy was unique in that it ran static analysis first before passing the findings to dynamic analysis. The static processes covers simple XOR; ROL; ROR encryption; packer detection; signature scanning; shellcode detection; meta data analysis; entropy and crypt-analysis, and file version detection.
Analysis sandboxes already existed but Sasi said that dynamic analysis in these environments took up to four minutes to process a sample.
The sandboxes may also lack the right software to analyse the samples, could be stumped by exploit language checks and other missing template and parameter requirements.
"The final aim of Sandy is to take in file formats and [reveal] the binary, controllers embedded inside it and [provide] attribution."
While malware sandboxes could analyse blindly-submitted binary samples, specific criteria were required for exploit sample analysis.
"A document exploit might only work on Chinese XP box or a Java exploit [might] only drop files on Mac machine."
He demonstrated analysis of a string of known Java vulnerabilities, some used in sophisticated attacks including waterhole campaigns targeting Tibetan groups.

.png&h=140&w=231&c=1&s=0)

_(23).jpg&h=140&w=231&c=1&s=0)






 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



