Google says its strengthened anti-phishing measures are being effective, and led to a quarter fewer attacks on users by nation-state threat actors in 2019.
Tony Gidwani, a security engineering manager at Google's Threat Analysis Group, posted updated statistics that showed the online giant had detected and sent out around 40,000 phishing alerts last year, down nearly 25 per cent on 2018.
"One reason for this decline is that our new protections are working—attackers' efforts have been slowed down and they’re more deliberate in their attempts, meaning attempts are happening less frequently as attackers adapt," Gidwani wrote.
In October 2017, Google launched the free Advanced Protection Program (APP) for frequently targeted users such as journalists, government workers, and human rights activists with tightened access controls for online services and hardware backed security, to mitigate against phishing attacks.
APP was expanded to Apple iOS devices in January this year, and Gidwani said Google has yet to see people enrolled in the program being successfully phished.
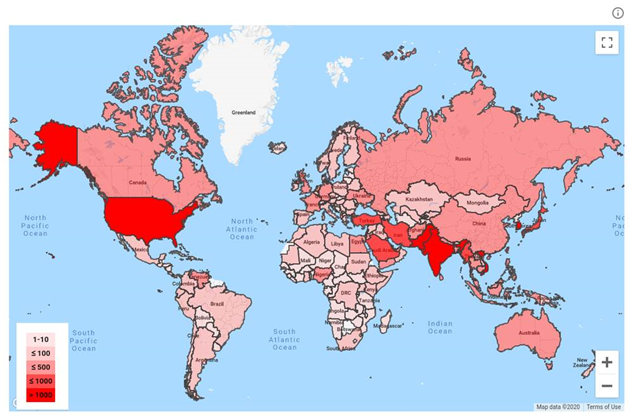
Up to 500 government-backed phishing attacks were recorded in Australia and New Zealand last year by Google's TAG.
Google did not provide information on where the attacks on Australian and New Zealand users originated from, nor did it give further detail on who were targeted.
TAG pays particular attention to dangerous zero-day attacks that attempt to exploit unknown software flaws.
Last year, TAG found multiple zero-day vulnerabilities in Google's Android operating system, its Chrome web browser.
The TAG security researchers also found zero-days in Apple's iOS and Microsoft's Windows operating systems.
Due to the danger unknown vulnerabilites present to users, vendors get seven days to patch or warn users about zero-days, or TAG will release an advisory about them.
On one occasion last year, TAG found a threat actor targeting North Korean users and individuals who work on issues relating to the country with no fewer than five zero-days.
The attacker attempted to exploit the vulnerabilities through email attachments or so-called spearphishing, as well as by compromising legitimate web sites and setting up malicious ones that targets were tricked to visit.
Google did not reveal which country the five zero-day attacker was from.
Gidwani said however that Russian government-backed attackers like the Sandworm/Iridum threat actor repeatedly go for geopolitical rivals, officials, journalists, dissidents and activists.
A rising number of attackers including Iranians and North Koreans have started impersonating news media and journalists, Gidwani said.
The attackers pretend to be journalists in order to seed false stories and disinformation with other journalists.
They also seek to build a rapport with journalists or foreign policy experts by sending several benign emails at first, and then following up with messages containing malicious attachments, Gidwani warned.
TAG is also seeing government threat actors using the novel coronavirus pandemic as lures, and will provide details on this activity at a later stage.


_(23).jpg&h=140&w=231&c=1&s=0)

_(28).jpg&h=140&w=231&c=1&s=0)
_(22).jpg&h=140&w=231&c=1&s=0)



_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition












_(1).jpg&h=140&w=231&c=1&s=0)



