A security researcher has found that a popular personality test app running on Facebook contained an easily exploitable flaw that could be used to expose sensitive information on tens of millions of users.
Belgian security researcher Inti De Ceukelaire joined Facebook's bug bounty program, set up by the giant social network after the Cambridge Analytica data leak scandal and tried out the NameTests.com's personality test app developed by Social Sweethearts.
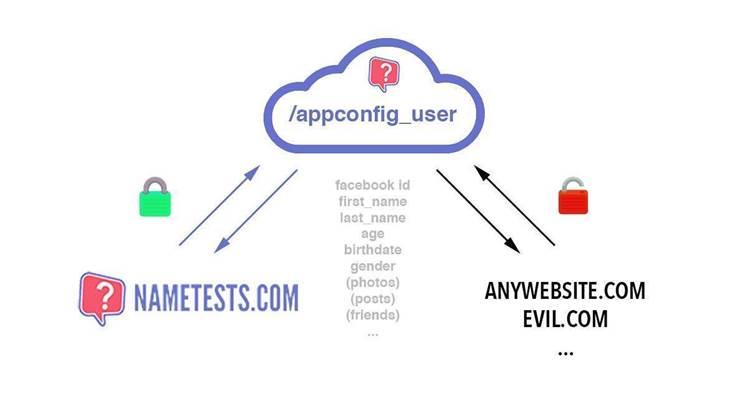
De Ceukelaire discovered that when he loaded a personality test, NameTests.com fetched his personal data from Facebook and displayed it on a webpage.
He was shocked to see that users' personal data was wrapped in a Javascript file by NameTests.com, which could be accessed via a weblink over the plain text HTTP protocol.
This meant that any website that requested the file could access the personal information retrieved from users' Facebook accounts.
The security researcher tested this by setting up a website that connected to NameTests.com and was able to access Facebook posts, photos and friend lists belonging to visitors.
Information leaked included people's Facebook IDs, first and last names, languages used, gender, date of birth, profile pictures, cover photo, currency, devices used, and much more.
Worse, De Ceukelaire found that NameTests.com doesn't log off users which means the site would continue to leak user data even after the app was deleted.
While the security researcher made it clear that only users that visited an attacker's website would have their data leaked, the flaw in NameTests.com has been around since the end of 2016.
NameTests.com has over 120 million monthly users, and generates more than three billion pages views a month.
De Ceukelaire contacted NameTests.com which said that to their knowledge the flaw had not been abused.
However, the flaw was very easy to spot and, given the large number of monthly users and page views, De Ceukelaire said he would be surprised if nobody had found the bug earlier.
He suggested users should be wary of giving new apps access to their data, and to delete any apps not in use, as well as removing browser cookies on a regular basis.
Facebook acknowledged the flaw and paid De Ceukelaire a US$8000 (A$10,888) bug bounty that was donated to the Freedom of Press Foundation.


_(28).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)

_(36).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



