An internet marketer has documented how to manipulate the back button in Google Chrome, the world's most popular web browser, to record how users interact with competitors' websites.
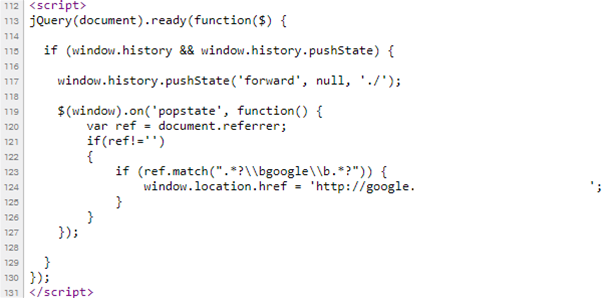
Dan Petrovic of Australian internet marketing firm Dejan wrote a Javascript that causes the back button in users' browsers to send them to a copy he had taken of a Google search engine results page (SERP).
Users would initially land on Petrovic’s home page referred to there by Google searches. Clicking on the back button in Chrome would normally return them to the search results Google had found, but Petrovic was able to change this behaviour and redirect them to a SERP clone on his own domain.
Once on Petrovic's copy of the SERP, if the user clicked on any links to competitor sites, he would be able to automatically record heat and scroll maps, as well as record mouse movements, clicks and text entry.
Alarmingly, Petrovic said he "gasped when I realised I can actually capture all form submissions and send them to my own email [address]."
Petrovic added that he never actually tried to do that.
Only about half of users visiting the bogus pages spotted anything suspicious, Petrovic said.
He put it down to using TLS-secured HTTPS pages lulling people into a false sense of security, saying "many users are just happy to see the padlock in their browser."
Petrovic also said that while Google tracked down his text site and de-indexed the entire internet domain it was hosted on, no penalty was issued to him.
Google's algorithms should be able to detect and similar tactics and penlise sites that use it, Petrovic said. Those still found in Google's search results should be labelled with "this page may be harmful" notices, he believes.
Furthermore, Petrovic said it shouldn't be possible to manipulate the behaviour of the back button in Chrome like this.
Petrovic copped criticism from security researchers for not following responsible disclosure protocol before publishing the flaw, and notifying Google to give the company a chance to respond, and if it wanted to, fix the problem.
Nevertheless, Petrovic's critics recognised that he is not a security professional, and acted with good intent.
Petrovic acknowledged the criticism that he acted unethically and even illegally by running the back button test on a live site without warning users with for instance a pop up, and denied he intended to exploit the method.
Instead, Petrovic said his motivation was "intellectual curiosity".





_(22).jpg&h=140&w=231&c=1&s=0)




_(26).jpg&w=100&c=1&s=0)
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition












_(1).jpg&h=140&w=231&c=1&s=0)



