
Researchers have gained access to user account details on a Google production server by exploiting a vulnerability in Cupertino's new developer service.
The white hat security professionals targeted the Google Toolbar Button Gallery used to allow developers to customise the icons that appear in browser toolbars.
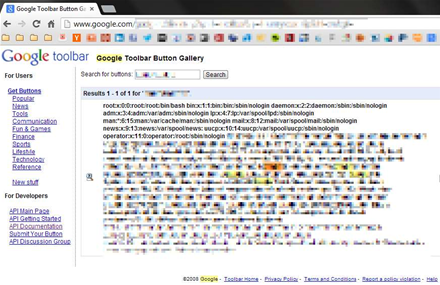
It took only one attempt to upload a malicious XML document and gain read access on Google's production server for the etc/passwd and etc/hosts.
The etc/passwd is a list of accounts containing user and group identities and home directory (passwords are usually stored in etc/shadow) while etc/hosts maps hostnames to IP addresses.
Google's etc/passwd
"What you see here is the /etc/passwd and the /etc/hosts of one of Google’s production servers," Fredrik Almroth, engineer at Swedish security consultancy Detectify said.
"We could just as well have tried to access any other file on their server, or moved on to SSRF exploitation in order to access internal systems.
"To (sic) say the least, that’s pretty bad."
Together with company co-founder Mathias Karlsson, the researchers discovered a dangerous XML External Entity (XXE) Processing vulnerability in the new Google service.
The flaw can lead to denial of service, remote code execution and the disclosure of local sensitive data including passwords, and could also allow attackers to pivot to other parts of the targeted network.
The magnitude of the attack could have been increased by delving deeper into Google's infrastructure if the researchers opted to exploit server side request forgery (SSRF), they said.
"The root cause of XXE vulnerabilities are naive XML parsers that blindly interpret the DTD (document type definition) of the user supplied XML documents. By doing so, you risk having your parser doing a bunch of nasty things. Some issues include: local file access, SSRF and remote file includes, denial of service and possible remote code execution."
Google's bug bounty security team in it's characteristic quick humour responded to the vulnerability with an animated meme, advising the researchers that their nasty bug would earn them US$10,000 (A$10,645).
"Google financed an awesome road trip for the team," Almroth said.
The payment spurred typical debate of whether tech mammoth Google should pay more for bugs that could result in havoc if it was instead quietly exploited by criminals.
OWASP has issued advice on how to secure XML parsers and defend against the attack.




_(36).jpg&h=140&w=231&c=1&s=0)
_(37).jpg&h=140&w=231&c=1&s=0)






 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



