Microsoft claims it has seriously damaged botnets using the Zeus keylogging Trojan source code in its fourth botnet takedown action last Friday.
Zeus, which Microsoft suspects infected 13 million Windows machines since it first emerged in 2007, was noted for its ability to log keystrokes, causing millions in damages in online banking, e-commerce and identity fraud.
Escorted by US Marshals, Microsoft, Financial Services – Information Sharing and Analysis Center (FS-ISAC) and NACHA – The Electronic Payments Association seized Zeus command control infrastructure at two hosting sites last Friday.
The two other bot operations targeted included Zeus' spawn, SpyEye and Ice-IX.
The raids followed Microsoft’s successful complaint lodged March 19, against 39 unidentified “John Doe” suspects, in which it appealed to the US District Court for the Eastern District of New York to allow the seizure of command and control servers at two locations in Scranton, Pennsylvania and Lombard, Illinois.
Microsoft accused three "John Does" of being the creators of the Zeus botnet, while the remaining 36 supported the operation by recruiting money mules, coding, and acquiring domain names and IP addresses.
The creators were accused of running a “racketeering enterprise” from about October 2010.
Richard Boscovich, senior attorney for the Microsoft Digital Crimes Unit (DCU), said it relied on the US Racketeer Influenced and Corrupt Organizations (RICO) Act, apparently often used against organised crime, to cast a wider net on Zeus-affiliated suspects.
The complaint, for example, identifies several money mules in the US and Britain, with one allegedly promoting a cash-out service “Hot Spot”, while John Doe 16 allegedly purchased the Zeus code and number 18 allegedly tested merged “Zeus/SpyEye” code.
“By incorporating the use of the RICO Act, we were able to pursue a consolidated civil case against everyone associated with the Zeus criminal operation, even if those involved in the “organization” were not necessarily part of the core enterprise,” said Bosovich.
“With this action, we’ve disrupted a critical source of money-making for digital fraudsters and cyberthieves, while gaining important information to help identify those responsible and better protect victims,” said DCU's Boscovich in a statement.
“The Microsoft Digital Crimes Unit has long been working to combat cybercrime operations, and today is a particularly important strike against cybercrime that we expect will be felt across the criminal underground for a long time to come.”
The three botnets were said to be responsible for almost “half a billion dollars” in damages, although the complaint only alleged the theft of “over $100 million” over five years.
Bot operations
Microsoft’s 40 page complaint [pdf] notes that Zeus and SpyEye merged in October 2010. Ice-IX emerged in May 2011, but was built on Zeus code with “enhancements to avoid virus-scanning software”.
“SpyEye was originally set up as a competitor to ZeuS and even went as far as to remove ZeuS if it found it on a computer that SpyEye was trying to infect,” Trend Micro security researcher Rik Ferguson noted.
“More recently the two code bases have been merged into a single piece of crimeware.”
Not all Zeus affiliated botnets were taken down, only some of the worst known ones, according to Finnish security vendor F-Secure, which supported Microsoft’s complaint.
Boscovich notes it only took two IP addresses behind Zeus’ command infrastructure and now monitors and additional 800 domains.
“Due to the unique complexity of these particular targets, unlike our prior botnet takedown operations, the goal here was not the permanent shutdown of all impacted targets," Boscovich notes on the DCU blog.
"Rather, our goal was a strategic disruption of operations to mitigate the threat in order to cause long-term damage to the cybercriminal organization that relies on these botnets for illicit gain.”
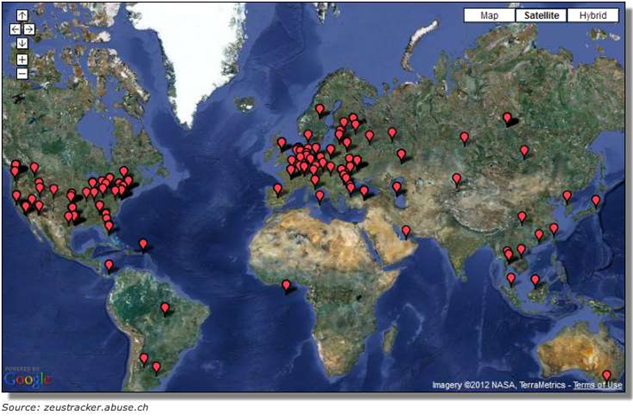
F-Secure shows a map of 350 Zeus command and control servers that remain online, including one in Melbourne, Australia.
It credited US-based security firm Kyrus Tech Inc, which reverse engineered and rebuilt Zeus using 70 Zeus binaries Microsoft supplied it.
The FBI in concert with European authorities in 2010 arrested 10 people in the US affilliated with Zeus, and at the time were seeking 17 others, issuing a “wanted” poster for the remaining members.
The suspects, mostly from Eastern Europe, were accused of attempting to steal $220 million via Zeus infected computers.


_(33).jpg&h=140&w=231&c=1&s=0)


_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



