Compromised OAuth tokens through a third-party app have resulted in large-scale data raids on instances of the Salesforce customer relationship management (CRM) platform, by an unknown threat actor.
GTIG
The third-party app is Salesloft Drift, which is described as a revenue orchestration platform that uses purpose built artificial intelligence (AI).
Salesloft has acknowledged the data breach, which started on August 8, and said it has notified all impacted customers.
How the threat actor, tracked as UNC (uncategorised) 6395, obtained the OAuth tokens from Salesloft to exfiltrate data from customer Salesforce instances wasn't detailed.
Salesloft said it has engaged a third-party digital forensics and incident response team to investigate the incident, and is working in collaboration with Salesforce to provide all customers with detailed information on attacker actions in their respective environments.
Analysing the incident, Google's Threat Intelligence Group (GTIG) and in-house Mandiant security team said "the [threat] actor systematically exported large volumes of data from numerous corporate Salesforce instances".
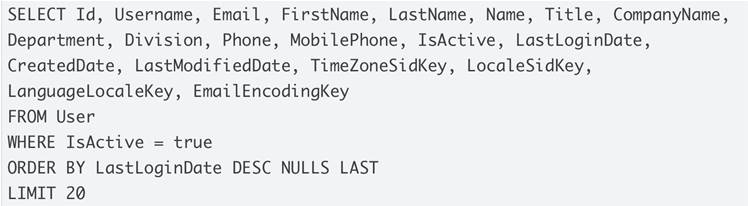
GTIG and Mandiant did not say how much data had been exfiltrated, and from which customers; the queries made by the threat actor focused on obtaining record counts from Salesforce objects, followed by other user data such as email address, login dates and contact information.
Secrets such as Amazon Web Services AKIA access key identifiers, Snowflake logins and passwords and other credentials were targeted by the attackers, GTIG said, with UNC6395 deleting the queries for them, which were nevertheless logged and available as evidence.
All active Salesloft access tokens have been revoked and refreshed for the Drift application, and administrators must reauthenticate with Salesforce to restate the third-party app integration.
Salesforce has also removed Salesloft Drift from its AppExchange, pending an investigation.
Open Authorisation protocol tokens allow third-party applications to access data on services, without requiring passwords.
GTIG and Mandiant did not connect the attacks to any particular organisation, but United States media reported the ShinyHunters/Scattered Spider threat actors have taken responsibility for the Salesloft intrusions.
ShinyHunters has been actively attacking Salesforce instances for the past few years, to extort organisations into paying ransom for the data in Bitcoin cryptocurrency.
Reported in June this year and continuing until early August, GTIG warned of a "vishing" (voice phishing) campaign by ShinyHunters, tracked as UNC6040/6240.
The vishing attack uses social engineering to obtain user credentials, allowing the threat actor "significant capabilities to access, query and exfiltrate sensitive information from the compromised Salesforce customer instances," GTIG said.
During the vishing, staff are tricked into connecting a malicious version of Salesforce's Data Loader data import/export application with OAuth to victims' environments, GTIG said.
Google's corporate Salesforce instance was hit by UNC6040 activity in early August, resulting in some data such as business names and contact information being extracted.


.png&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)







 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



