The United States Department of Homeland Security has issued an emergency directive in response to a serious, global campaign of domain name system (DNS) infrastructure tampering, believed to originate in Iran.
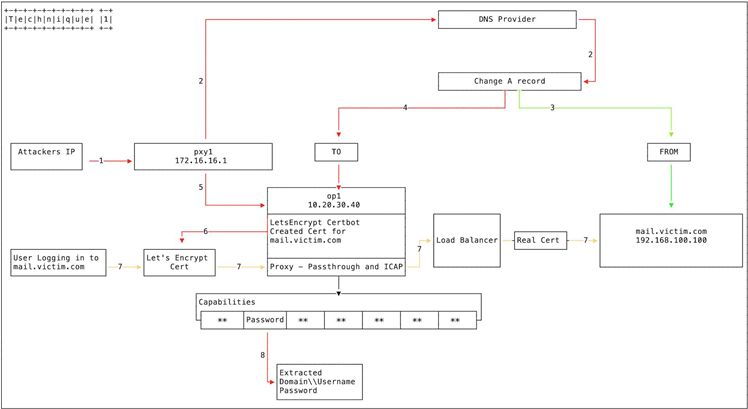
Earlier in January, security vendors Cisco Talos and Mandiant FireEye outlined a spate of DNS hijacks against multiple government, telcos and internet infrastructure organisations in Europe, North America and the Middle East/Africa.
Attackers have successfully redirected web and email traffic by altering DNS records, making them point to servers on addresses that they control.
They've been able to do so by capturing administrative credentials for administrative accounts that can make changes to DNS records. FireEye and Talos said they have received reports that sophisticated phishing attacks were used to gain acccess for DNS record manipulation, as well as compromising a victim's domain registrar account.
Once attackers have changed DNS records, they've also been able to obtain valid digital encryption certificates for an organisation's domains. This allows attackers to decrypt user data undetected.
FireEye and Talos said its initial research suggests the actors responsible for the attacks that have taken place over a year "have a nexus to Iran".
Federal agencies are now required to take action as per the DHS directive to mitigate against the DNS attacks.
Within ten business days US federal agencies with .gov and other domains must audit publci DNS records to verify that they point to the correct, intended location. If they do not, agencies must report it to the Cybersecurity and Infrastructure Security Agency (CISA).
To prevent future unauthorised DNS account accesses, agencies must change passwords on these and add multi-factor authentication.
CISA's Cyber Hygiene service will also begin a regular delivery of newly added certificates to Certificate Transparency log for US federal agency domains.
Agencies are required to immediately start monitoring CT log data for certificates that they did not request. If any unauthorised certificates are found, they must be reported to the issuing certificate authority and the CISA.
The Australian Cyber Security Centre issued an advisory yesterday recommending that administrators review the FireEye and Cisco Talos blogs for information on how to harden their organisations' DNS infrastructure.
ACSC head Alastair MacGibbon also encouraged administrators to follow the agency's Essential Eight mitigation strategies to better safeguard their systems.



_(37).jpg&h=140&w=231&c=1&s=0)







 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



