Users of Microsoft's Skype communications program are being targeted by a new malware which attempts to intercept audio, video, and chats.
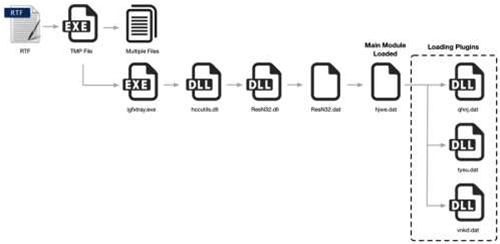
The so-called T9000 malware also takes regular screenshots of video calls, and attackers can use it to collect document files - even those being shared via removable drives.
According to security vendor Palo Alto Networks, the T9000 spyware is a newer version of the APT T5000 from 2013, which is also known as Plat1 or Grand Theft Auto Panda, and runs on the Windows operating system.
T5000 was used to attack human rights activists and the car industry, according to security firm Cylance. It was also used in spearphishing attacks in 2014, targeting people interested in the disappeared Malaysian Airlines flight MH370, according to FireEye.
In comparison, T9000 is more advanced than T5000, according to Palo Alto Networks.
The firm said it has seen the malware being used in several targeted attacks against organisations in the United States, and its analysis shows that T9000 is designed to be used against a broad range of victims.
T9000 is dropped via a rich text format file with an exploit for CVE-2012-1856, which affects an ActiveX control in Microsoft Office, older versions of SQL Server, and other Microsoft products.
It also contains an exploit for the newer CVE-2015-1641 vulnerability, which allows attackers to execute arbitrary code via specially crafted RTF files.
Once planted on a victim system, T9000 attempts to hide itself from detection and checks for the presence of 24 to 27 different anti-virus products before full installation. If it discovers a listed security product, T9000 will customise the installation mechanism to avoid the defences.
T9000 also contains checks during installation to see if a security researcher is analysing the malware.
The malware can receive several commands remotely to execute on victim machines, such as listing directories, uploading and deleting files, and more.
Palo Alto Networks has identified the functionality of ten T9000 commands, with a further 14 yet to be fully discovered, the vendor said.
Update: A Microsoft spokesperson said updated versions of Windows and Office, as well as Skype, are not vulnerable to the exploits used by T9000.
"To further protect our customers, we’ve added detection for the malicious software known as ‘T9000’ to Windows Defender," the spokesperson said.
"Customers that have installed security updates released in 2012 (MS12-060) and 2014 (MS14-033), either manually or by enabling automatic updates, will already be protected. Our recommendation is to enable automatic updates, which installs the latest security protections, and use the latest version of Skype.”





_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



