A data breach that saw Russian government-mandated remote access credentials for local and foreign businesses leak onto the internet took almost three years to plug, a security researcher says.
Dutch security researcher and former GDI Foundation chairman Victor Gevers told iTnews his team found the remote access credentials in unsecured MongoDB instances operated by Russian companies.
"Kremlin demands remote access to systems, and we started paying attention to this detail after finding more MongoDBs belonging to Russian companies," Gevers explained.
The credentials were found in thousands of open databases, and the Kremlin reused them everywhere, leaving a large number of businesses open to access from the internet.
Gevers reported the data breaches to Russian authorities and the companies operating the MongoDB servers in 2016 but said the issue took "three years, five months and 15 days" to fix.
Among the companies impacted were large Russian telco TTK, which left its network operations centre and security information and event management (SIEM) platform exposed to the internet.
American companies like Disney that operate in Russia and are compelled to provide remote access to their systems were accessed using the same credentials, Gevers noted.
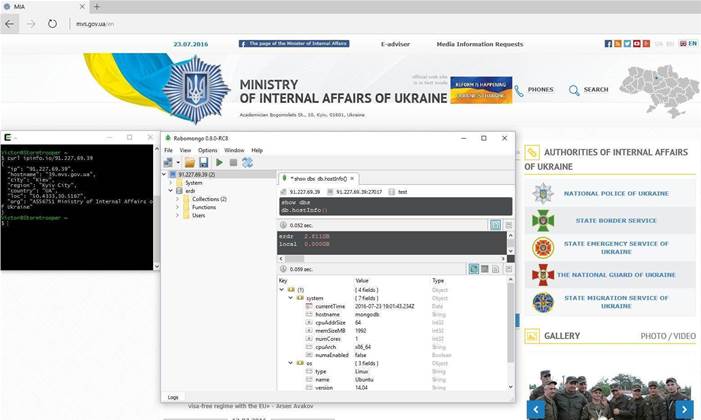
One open database that contained the Kremlin credentials was a MongoDB server holding electronic raw data reporting information belonging to the Ministry of Internal Affairs of Ukraine, a country that Russia is at war with.
Gevers suggested companies that are subject to enforced remote access regulations such as those of Russia take steps to have the credentials secured.
"The bottom line is if you let a government choose a password, make sure they don't use the same credentials or password formula the same way over and over," Gevers said.




_(37).jpg&h=140&w=231&c=1&s=0)
_(36).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



