Cyber security researchers have uncovered a sophisticated distributed denial-of-service (DDoS) operation that they say blurs the line between traditional malware and modern software-as-a-service (SaaS) platforms.
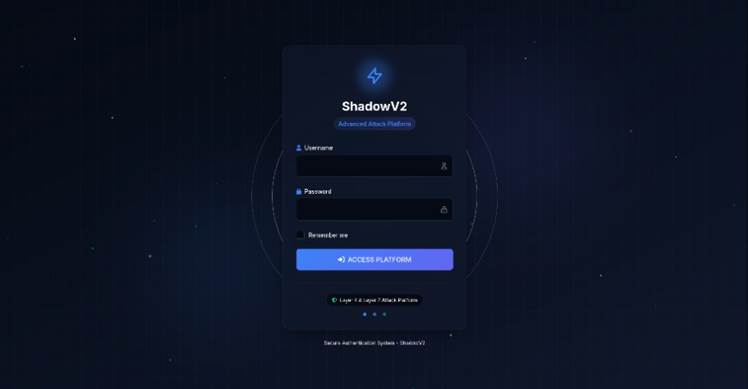
The ShadowV2 botnet, identified by security vendor Darktrace, offers attackers a professional login panel, polished user interface with a portal, and tools that mirror legitimate cloud-native applications.
Researchers found the platform built around a FastAPI and Pydantic backend, complete with OpenAPI documentation, and a front-end styled with Tailwind cascading style sheeets (CSS) animations, Darktrace said.
The system is billed as an “advanced attack platform” and includes role-based access controls, user management, and blacklists for protected targets.
While its main domain shows a fake law enforcement seizure notice, the underlying application programming interface endpoints remain fully operational.
ShadowV2 makes advanced DDoS techniques available to attackers, including HTTP/2 rapid reset floods, Cloudflare’s “under attack mode” bypass, and large-scale HTTP request storms.
The HTTP/2 rapid reset method exploits multiplexing to generate thousands of requests per connection, cancelling them instantly to allow more.
This enables a single client to push far more traffic than older flood techniques.
The platform also bundles a ChromeDP browser to attempt Cloudflare JavaScript challenge bypasses, although headless browser detection limits its success.
Behind the scenes, the operation runs on a Python-based command-and-control framework hosted in GitHub CodeSpaces, Microsoft’s cloud development environment.
By using CodeSpaces, the attackers gain Microsoft’s global infrastructure, reduce overhead, and conceal operations behind legitimate cloud terms of service.
Targets include exposed Docker daemons on Amazon Web Services (AWS) EC2 instances, suggesting the operators have detailed knowledge of how cloud workloads are commonly deployed.
Darktrace first saw attacks against its honeypots on June 24, with malware samples appearing soon after on Google's VirusTotal scanning site, from United States and Canadian sources.
The timing indicates either victims uploaded samples for analysis or the attackers were testing detection rates.
What stands out is the level of software engineering.
Environmental variables are used for configuration, RESTful APIs with one-second heartbeats for bot management, modular design for fast updates, and detailed error handling.
These practices resemble those of legitimate technology firms rather than underground hackers.
By embedding their infrastructure within platforms like GitHub CodeSpaces, the operators complicate attribution and takedown, while raising the bar for defenders.
Traditional signature-based security tools struggle against adversaries who adopt cloud-native architectures and professional development practices.
Darktrace researchers warned that the presence of user tiers and attack limitations indicates a service model aimed at different customer segments, potentially widening its reach beyond traditional cybercriminal groups.



_(28).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



