A group of researchers from US and Chinese universities claim to have discovered serious, high-impact vulnerabilities in Apple's OS X and iOS operating systems that permit attackers to bypass application isolation to fully expose sensitive user data.
In their paper, the researchers honed in on an earlier discovery that Android apps can break out of their "sandboxes" with minimal privileges in order to isolate them from other apps and the operating system itself.
Sandboxing is part of most mainstream operating systems, but the researchers believe the effectiveness of the technique has not been fully understood due to the complexity of a modern OS.
Unless developers assume that all apps, even when they belong to the same user, should treat each and every one as untrusted and perform proper security checks during interactions with one another and the operating system, gaping security holes could open up, the researchers found.
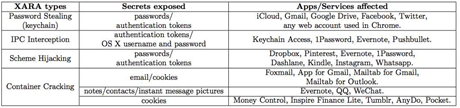
Abusing this trust with a vulnerability concept the reseachers called unauthorised cross-app resource access - XARA - could provide attackers with full access to user data on OS X and iOS, which are considered to be more secure than Android.
"The consequences of such [XARA] attacks are devastating, leading to complete disclosure of the most sensitive user information (eg. passwords) to a malicious app even when it is sandboxed," the researchers said.
They were able to assemble a sandboxed app that successfuly retrived iCloud passwords and security tokens from the OS X 10.10.3 system keychain credentials store, as well as login details stored by other apps.
XARA can also break Apple's multi-layer defence and get through restrictive app vetting on the App Store, allowing attackers to upload malicious programs unnoticed.
The researchers claimed they were able to upload several XARA attack apps to the Apple App Store and have them approved. They were removed after testing was completed.
iCloud authentication token theft from the OS X Keychain database.
iOS does not have the full functionality of OS X and is less vulnerable, but not immune to XARA attacks, the researchers said. The iOS scheme interprocess communications channel in particular can be hijacked in the same manner as under OS X, they found.
XARA appears to be a case of a classic "resource squatting" problem when software does not verify which party owns a piece of a critical resource, extended to interaction between third-party apps, according to the researchers.
Mitigating against XARA is difficult, as the operating system usually doesn't know how to protect third-party app resources or communication.
To avoid XARA vulnerabilities, the researchers suggested redesigns of OS X and iOS to introduce authentication to verify resource sharing and app communication. Security checks should also be mandatory with developers given the opportunity in the OS to perform them.
The researchers built a scanner to automatically analyse OS X and iOS specific binaries to check if they had protection against XARA attacks, and found a large number of popular apps are vulnerable.
Apple was notified of the XARA vulnerabilities in October last year, and asked the researchers not to publish their work for six months. The researchers have not had any further communication from Apple since then.


_(20).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)






 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



