Security researchers are watching the infrastructure of malware delivery botnet Emotet being compromised by an unknown actor, and disrupting the criminals' activities in the process.
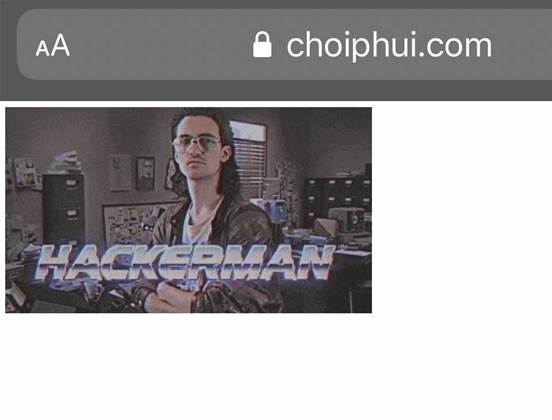
Microsoft cyber security researcher Kevin Beaumont wrote that someone is currently replacing the malware files distributed by Emotet with animated GIF images.
The images include one of Hackerman, who starred in the internet cult classic Kung Fury.
Beaumont last year discovered that the Emotet gang used a very insecure payload distribution method.
This involves the Emotet criminals using hacked Wordpress sites for storing the malware files users are tricked into executing.
To manage the distribution of malware, the Emotet gang leave an open source webshell application on the sites for access and control.
"Their passwords and techniques for this are known. The net impact is anybody can replace their payloads," Beaumont said.
Around a quarter of all Emotet distributed malware payloads have been replaced in an automated fashion, Beaumont and other researchers estimate.
Instead of executing the malware when users click on links in phishing emails, an animated GIF displays in the user's browser.
Those giphy's must have spooked Ivan. He orphaned an entire week's worth of tier 1 infrastructure on a Thursday morning.
— Erik Fichtner (@unixronin) July 23, 2020
Good game, mystery hero.
Currently, there's no indication as to who is disrupting the Emotet operation.
Beaumont speculated that it might be the Emotet criminals themselves, or other threat actors trying to sabotage the botnet.
Security researchers could also be behind disrupting Emotet, Beaumont speculated.
While acknowledging that Emotet is being directly impacted by the attack, Beaumont cautioned that anybody could replace the payloads for other malware that's less detectable.
Emotet had been quiet for several months until recently when Microsoft Security Intelligence noted the botnet had resurfaced with a massive email campaign.
Emotet resurfaced in a massive campaign today after being quiet for several months. The new campaign sports longtime Emotet tactics: emails carrying links or documents w/ highly obfuscated malicious macros that run a PowerShell script to download the payload from 5 download links pic.twitter.com/FZJqDCJQGV
— Microsoft Security Intelligence (@MsftSecIntel) July 17, 2020
The botnet is believed to have distributed the malware used to attack 19 organisations in Australia last year.

.png&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)






.png&w=120&c=1&s=0) Tech in Gov 2025
Tech in Gov 2025
 Forrester's Technology & Innovation Summit APAC 2025
Forrester's Technology & Innovation Summit APAC 2025
.png&w=120&c=1&s=0) Security Exhibition & Conference 2025
Security Exhibition & Conference 2025
 Integrate Expo 2025
Integrate Expo 2025
 Digital As Usual Cybersecurity Roadshow: Brisbane edition
Digital As Usual Cybersecurity Roadshow: Brisbane edition




.jpg&h=271&w=480&c=1&s=1)






.jpg&h=140&w=231&c=1&s=0)



