Microsoft has rushed out security updates for a remotely exploitable vulnerability in the Windows System Message Block version 3 file sharing protocol that researchers said could be abused to create self-spreading "worms" like the 2017 WannaCry malware.
After leaking information this week of the vulnerability as part of its regular Patch Wednesday round of updates to security vendors who published details about it, Microsoft was only able to provide a partial workaround for the critical flaw for Server operating systems.
Windows clients with SMBv3 remained vulnerable to exploitation.
Updates for Windows 10 32 and 64-bit systems and Windows Server are now available from Microsoft, which it strongly recommends users to install them as soon as possible.
Security researchers noted that the vulnerability, known as EternalDarkness and SMBGhost as it doesn't require authentication by attackers, could be used to create self-replicating malware, so-called worms.
Microsoft has shipped an emergency, out-of-band patch for a critical RCE vulnerability in Server Message Block 3.0 (SMBv3)
— Ryan Naraine (@ryanaraine) March 12, 2020
Bulletin here: https://t.co/vNbMFfnB2M
���� Treat as highest possible priority
Kryptos Logic security researcher, Briton Marcus Hutchins who rose to fame during the 2017 WannaCry worm epidemic that cost vast financial damage, analysed the flaw and found it to be similar to the earlier Remote Desktop Protocol DejaBlue one.
Now patch is out: compressed packet specifies its' uncompressed size, which is added to an offset and used to calculate the allocation size (resulting in an int overflow). Interestingly, this bug is identical to the "DejaBlue" RDP RCE I documented here: https://t.co/dBajgXoZ7O
— MalwareTech (@MalwareTechBlog) March 12, 2020
DejaBlue along with another wormable flaw, Bluekeep, were discovered last year and Microsoft issued patches for them in September.
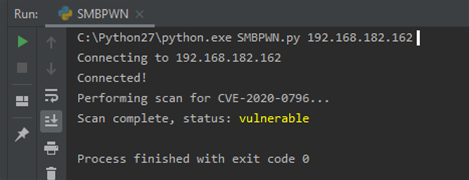
Hutchins has written a proof of concept script for CVE-2020-0796 that can be used to generate denial of service attacks on vulnerable systems.
His employer Kryptos Logic scanned the internet and found some 48,000 vulnerable hosts exposing the SMBv3 protocol to the world.



_(28).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



