Security experts are urging users of the popular WordPress publishing platform to update their installations, as site defacements grow at an alarming rate.
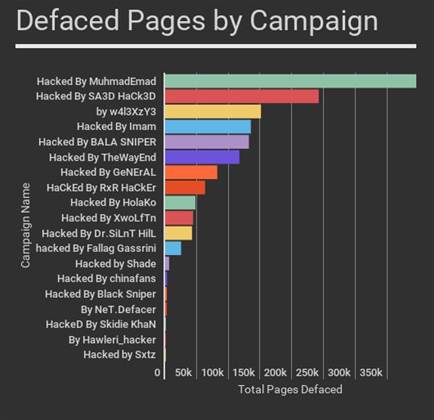
Research by WordPress security vendor Wordfence showed a 26 percent increase in defacement attacks in just 24 hours.
Wordfence counted close to 1.9 million WordPres sites, indexed by Google, as being defaced yesterday.
The hackers are posting political messages to support Kurdish Peshmerga fighting against the Islamic State and the Turkish army.
They are taking advantage of a vulnerability in the WordPress REST API to inject content.
The REST API is enabled by default on WordPress 4.7.0 and 4.7.1. Attackers can exploit the vulnerability to edit posts on a WordPress site.
While the flaw was publicised at the end of January - and WordPress issued a patch at the time, warning that earlier versions of the content management system contain a serious vulnerability - many sites have yet to update their installations.
Over the weekend, security vendor Sucuri warned it had observed remote code execution attempts that exploit the REST API vulnerability.
Sucuri advised users to turn off plugins that allow them to directly insert PHP scripting language code into posts, as they allow attackers to inject content into the WordPress site database. It also urged users to update to 4.7.2 immediately.




_(33).jpg&h=140&w=231&c=1&s=0)
_(36).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



