Computer giant Lenovo has come under fire from users and security pundits after its consumer laptops were found to contain pre-installed adware/malware which could be used to intercept and hijack encrypted Transport Layer Security communications in Microsoft Windows.

The ‘Superfish' adware is a third-party application that was, until last month, installed on all Lenovo consumer laptops. It is designed to inject ads into web sessions, send browsing information onto the ad company, and monitor user activity.
Superfish was not installed on Lenovo's business laptops.
The adware, developed by the company of the same name, also used its own fake, self-signed CA certificate to hijack user sessions over SSL/TLS, a fact that has security experts up in arms.
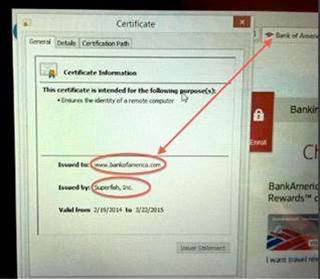
Source: Kenn White, Twitter
The above image, posted online by OpenCryptoAudit researcher Kenn White on Twitter, showed the difference between the Bank of America website URL and the fake certificate issued by Superfish.
Such X.509 digital certificates are used by websites to ensure communications are shared with the right authority.
In this case Superfish usurped that role, meaning it was essentially carrying out a man-in-the-middle interception attack to capture content that would otherwise be protected by SSL and TLS.
Digital rights lobby group Electronic Frontier Foundation called Lenovo's Superfish partnership "catastrophically irresponsible and an utter abuse of trust", as the MITM certificate can be used to intercept user data.
A copy of the Superfish private certificate key is stored on all adware-preloaded Lenovo laptops, and has been extracted by Errata Security researcher Rob Graham.
An attacker with the private key has full access to TLS encrypted and authenticated sessions, leaving a large number of Lenovo users worldwide open to interception.
Security pros react
Lenovo has subsequently urged users of affected laptops to remove the software, although numerous commentators say this won't fix the problem, as the certificate would still be on the system.
Worse still, on the same network, Lenovo laptops could apparently be used to attack each other.
Last month, a Lenovo administrator confirmed that the software had been “temporarily removed” from consumer devices until a software fix would be provided – although it's unclear how many devices have shipped with the adware.
“We have temporarily removed Superfish from our consumer systems until such time as Superfish is able to provide a software build that addresses these issues,” wrote Mark Hopkins.
“As for units already in market, we have requested that Superfish auto-update a fix that addresses these issues.”
Security researcher Marc Rogers said Lenovo's decision to pre-install Superfish was "unbelievably ignorant and recklesss".
"It's quite possibly the single worst thing I have seen a manufacturer do to its customer base. At this point I would consider every single one of these affected laptops to be potentially compromised and would reinstall them from scratch," he wrote on his blog.
Alan Woodward, Europol adviser and visiting professor at Surrey University's Computing Department, said it was unbelievable Lenovo had come to install this adware on users' machine.
“It's an open bit of software, SuperFish, within the browser and it issues its own fake certificate to intercept encrypted communications," he said.
“One can only assume their intention was helping users without understanding the technical details. It's evidence that the road to hell is paved with good intentions…and of marketing over security.”
Daniel Cuthbert, security researcher at Sensepost, sai the adware's use of a fake certificate would mean the compromise of all web encryption.
“In a nutshell, they are able to compromise all SSL. What this means is that Superfish is able to man in the middle SSL connections, access data and inject content into those streams.
“We aren't just talking about websites here, but anything that makes use of SSL. Some are calling it adware but this is plainly malware. As for exploitation, [it's] too early to tell, I'm afraid, but Superfish is already doing the exploitation on users laptops," he said.
“As for protection, never run the default install. Remove it and install fresh from source.”
Researcher Filippo Valsorda has set up a Certificate Authority test site for Superfish that allows users to find out if their systems are compromised with the adware.
Lenovo to stop pre-loading Superfish
Lenovo has since issued a statement reaffirming that Superfish was 'completely disabled' and no longer pre-loaded onto Lenovo machines since January.
"The relationship with Superfish is not financially significant; our goal was to enhance the experience for users. We recognise that the software did not meet that goal and have acted quickly and decisively."
It advised that Superfish may have appeared on certain models from its G Series, U Series, Y series, Z Series, S Series, Flex Series, MIIX Series, Yoga Series, and E Series laptops.




_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



