The Kaseya Virtual Systems Administration (VSA) remote management and monitoring system software that was hijacked in a devastating ransomware attack had multiple critical vulnerabilities, security researchers found.
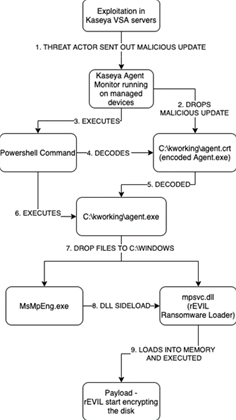
Researchers at the Dutch Institute for Vulnerability Disclosure (DIVD) found seven vulnerabilites in Kaseya VSA on-premise, and reported them to the vendor ahead of last week's REvil attacks worldwide.
Kaseya was quick to respond and to develop patches for four of the vulnerabilites but two critical bugs remain to be addressed.
"As we stated before, Kaseya’s response to our disclosure has been on point and timely; unlike other vendors, we have previously disclosed vulnerabilities to," DIVD researcher Frank Breedijk wrote.
One of the vulnerabilities reported by DIVD were used by the REvil ransomware criminals, in last weekend's attacks ahead of the 4th of July national holiday in the United States, DIVD said.
Kaseya patched a remote code execution vulnerability on April 10, and a Structured Query Language (SQL) command injection vulnerabilty along with a local file inclusion and Extended Markup Language external entity flaws on May 8 this year.
Three other bugs, a credentials leak and business logic flaw, a two-factor authentication bypass and a reflective, authenticated cross-scripting vulnerability in Kaseya VSA versions 9.5.6 and earlier still await patches.
The critical credentials leak vulnerability is rated as 10 out of 10, and the also critical 2FA bug is rated 9.9 out 10 on the Common Vulnerability Scoring System (CVSS) version 3.1 with low attack complexity and no user interaction required to exploit them.
DIVD said it is holding back from releasing full details of the vulnerabilities until such a time they have been addressed by Kaseya.
Separately, security vendor Trustwave's Spider Labs analysed the version of REvil malware used in the Kaseya attacks.
Trustwave found that the malware won't execute on systems that have Russian, Ukrainian, Belarusian and Romanian default languages set.
REvil also excludes former Soviet bloc nations in Central Asia, Caucasus as well as Syria.
Spammers are also attempting to exploit the Kaseya attacks with phishing emails that claim Microsoft has issued an update to protect against the vulnerability in the remote management and monitoring system, Trustwave warned.
Clicking on the links in the phishing emails could execute the CobaltStrike malware from a remote location, Trustwave said.




_(28).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



