A worm has been found attempting to hijack computers via the Remote Desktop Protocol (RDP) used commonly for tech support.

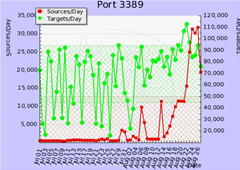
The SANs Institute Internet Storm Centre reported traffic over RDP had increased ten-fold which was a “key indicator that there is an increase of infected hosts that are looking to exploit open RDP services".
The worm, dubbed Morto or death, compromises Windows servers and workstations by scanning subnets for remote desktop connection and guessing administrator passwords such as ‘12345’, ‘server’ and ‘password’.
F-Secure technology chief Mikko Hypponen said that Amazon Web Services would likely be the most vulnerable target.
“Let's hope it won't be hit,” he said.
The worm could be used to launch denial of service attacks against targets nominated by command servers, Microsoft said in an advisory.
It attempted to terminate popular anti-virus programs including Sophos, McAfee, Symantec and Clam AV.
Users on a Microsoft security forum who noticed reams of outgoing 3389/TCP traffic reported that many anti-virus programs did not detect the worm. They said fully-patched systems were infected.
Once a connection had been made, Morto copied dll files to a temporary drive labeled A.
It contained an installer and a payload clb.dll file which executes in the Windows directory preferentially to the legitmate dll by the same name.
Microsoft recommended users use strong passwords, enable firewalls and update software and anti-virus.



_(37).jpg&h=140&w=231&c=1&s=0)






 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



