Users of Apple's macOS computers are being warned to stay on the lookout for two new strains of malware that have been dubbed the "most sophisticated" ever to hit the platform.
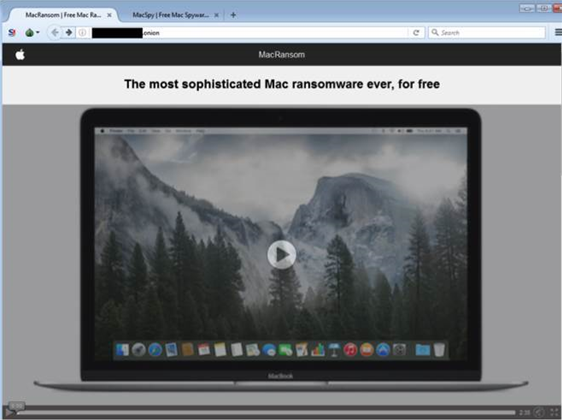
The MacSpy spyware and MacRansom ransomware as-a-service offerings went up for sale via The Onion Router (TOR) network on May 25.
Infosec firm AlienVault, which identified the MacSpy strain, said it was one of the first spyware-as-a-service offerings for the OS X / macOS operating system.
Security vendor Fortinet, which outed the MacRansom variant, similarly said this "could be the first time to see [ransomware-as-a-service] that targets macOS".
Both strains were likely created by the same malware developer in response to a lack of "sophisticated malware for Mac users", according to AlienVault.
The developer claims MacSpy is able to capture screenshots every 30 seconds, log every keystroke, access synced iPhone photos, record sounds continuously even without the microphone turned on, retrieve clipboard contents, and obtain history and download data from Safari and Chrome.
It can do so without 'any digital trace' to the malware operator, the developer claims. Further advanced features - like access to emails and social network accounts, retrieval of files, and encryption of the entire user directory - are on offer for an undisclosed number of bitcoins.
Similarly, MacRansom promises an "unbreakable" 128-bit industrial standard encryption algorithm that will leave the victim "no option but to purchase our decryption software".
The ransomware can encrypt an entire home directory "in under a minute" and similarly leaves no digital trace, according to the developer, who also said the RaaS is completely invisible until scheduled execution time.
MacRansomware demands 0.25 bitcoin (around A$926) to unlock encrypted files.
AlienVault and Fortinet said both strains of malware were likely created by an inexperienced coder, given a handful of issues they came across in attempting to buy and execute the spyware and ransomware.
However they warned that MacRansomware had the ability to permanently destroy user files if successfully deployed.
"A remarkable thing we observed when reverse-engineering the encryption/decryption algorithm is that the TargetFileKey is permuted with a random generated number," Fortinet said.
"In other words, the encrypted files can no longer be decrypted once the malware has terminated – the TargetFileKey will be freed from program’s memory and hence it becomes more challenging to create a decryptor or recovery tool to restore the encrypted files.
"Moreover, it doesn’t have any function to communicate with any C&C server for the TargetFileKey meaning there is no readily available copy of the key to decrypt the files."
It is technically possible to recover the TargetFileKey by by using a brute-force attack, Fortinet said.
"It should not take very long for a modern CPU to brute-force an 8-byte long key when the same key is used to encrypt known files with predictable file’s contents."
AlienVault said the best way to detect MacSpy was to use a combination of network IDS (NIDS) rules as it communicates.



_(23).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



