A hacking group has devised a unique technique that allows them to use a low-level Intel systems management feature to create a backdoor for the invisible transfer of files and malware, according to Microsoft security researchers.
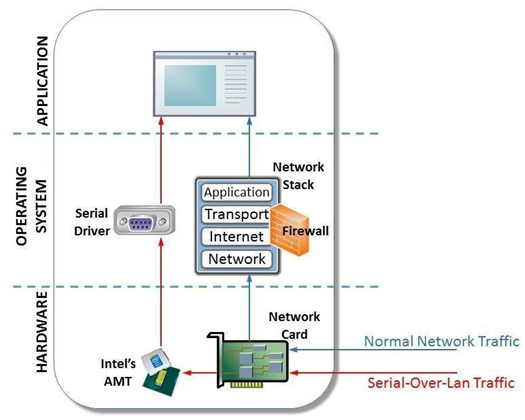
The group, called Platinum by Microsoft, has abused the Intel Active Management Serial-over-LAN feature on vPRo processors and chipsets to enable a silent communications channel for malware already planted on servers.
As the Intel AMT SoL feature works independently of, and outside the control of the computer operating system, Platinum was able to use it to bypass firewalls and security software that monitor traffic for anomalies.
The feature works even with the network card disabled, Microsoft said.
So far, the file transfer tool has been found only in a dozen systems.
The AMT SoL feature would be difficult to exploit on a larger scale, as it is not enabled by default and requires administrator privilege to be provisioned on workstations.
Microsoft said it is not known if Platinum was able to provision workstations with AMT SoL, or piggyback on it being previously switched on.
Platinum has been active in South East Asia since 2009, and conducts only a small number of targeted campaigns a year using advanced malware and zero-day attacks, Microsoft said [pdf].
The group seeks to steal intellectual property and conduct electronic espionage against governments and related organisations.




_(36).jpg&h=140&w=231&c=1&s=0)
_(37).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



