One of the world's most notorious providers of offensive information technology to governments has had its internal systems breached and customer documentation dumped on the open internet.
Hacking Team, founded in 2003 and based in Milan, Italy, provides surveillance software and intrusion tools to law enforcement agencies around the world.
On its website it boasts clients across the US, Europe and the Asia Pacific, assisted by more than 50 employees providing "all aspects" of offensive IT tools.
The company's primary surveillance tool - dubbed Da Vinci - earned it a spot on the Reporters Without Borders Enemies of the Internet list.
Its products allow governments to monitor online communications, record voice-over-IP (VoIP) sessions, remotely activate microphones and cameras, and break encrypted files and emails.
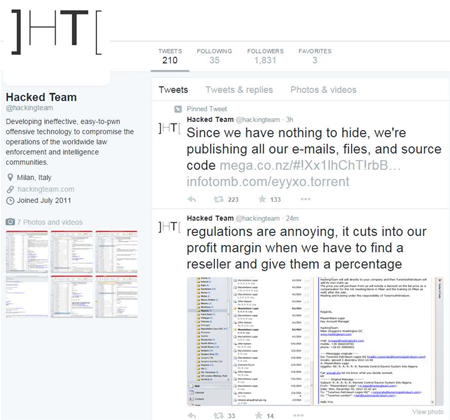
The company's Twitter account was today compromised, and around 400GB of internal emails, files and source code were leaked to the internet, and spread via social media.
The attackers also posted screenshots of the compromised data from the leaked file to Twitter, and defaced the company's logo and biography.
Earlier this afternoon - before his own Twitter account appeared to be hacked - Hacking Team engineer Christian Pozzi confirmed the breach and said the company was notifying affected customers and working with police.
According to the leaked data, Hacking Team counts customers from South Korea, Saudi Arabia, Lebanon, Egypt and Mongolia. The company has long maintained it does not sell to oppressive governments.
"Who says selling surveillance tech to govs that spy on journalists doesn't pay well? $1 million from Ethiopia," privacy researcher and activist Christopher Soghoian said on Twitter.
Australia is also listed as a customer of Hacking Team, according to the company's wiki.
A leaked client renewal list reveals the Australian Federal Police has made use of Hacking Team's technology in the past.
Spreadsheets contained in the data dump suggest the AFP paid for unspecified, offensive-use products from Hacking Team twice: once in November 2009 (A$126,525) and again in February 2010 (A$234,980) at a total of A$361,505.
The AFP is however listed as "expired" in the client renewal list. The force has long been a suspected customer of Hacking Team competitor FinFisher, which produces a set of spyware and intrusion tools for law enforcement.
Control nodes for FinFisher have previously been discovered in Australia, but the AFP has consistently declined to comment on its use of the technology.
The leaked documents indicate Hacking Team account manager Daniel Maglietta and then-colleague Serge Woon - both who appear to be based in Singapore - travelled to Sydney city for two days on business in May last year. The reason for the trip is unclear.
The Attorney-General's Department, Defence and the AFP have been contacted for comment, as have Australia's state police forces. NSW Police was last year outed as a user of FinFisher.
The AFP declined to confirm or deny "what may or may not form part of its operational or technical methodologies".
NSW Police told iTnews it had not - either currently or historically - used Hacking Team's products, but did not comment further.
A WA Police spokesperson said while the agency doesn’t disclose the nature of all software or service providers it uses, there was no indication it had employed Hacking Team's software.
NT Police assistant commander Kris Evans told iTnews some areas of policing "due to their very nature are required to remain covert". He declined to comment on whether his force had used Hacking Team's software.
Queensland Police said it doesn't disclose details of its software and service providers "of this nature" due to security sensitivities.
Tasmania Police said it wasn't a user of Hacking Team's products.
Victoria Police said while it doesn't disclose the nature of all software or services it uses, there appeared to be no relationship between the force and Hacking Team.
A Defence spokesperson said no agency within the portfolio had used the company's spyware.
It is unclear who is behind the Hacking Team attack.
With Juha Saarinen



_(36).jpg&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



