The Dridex banking trojan has reappeared after being largely unseen in major email campaigns for nearly a year, and is targeting Australian banking customers, according to security researchers.
Some lower-volume assaults retained use of Dridex during 2016, but many bad actors migrated to using the Locky ransomware for malicious campaigns.
That activity slowed in 2017, with most analysts agreeing that the takedown of the Necurs botnet contributed to the slowdown in the mass dissemination of both Locky and Dridex.
But researchers at Proofpoint are now reporting that two large-scale Dridex campaigns, which they've dubbed Dridex botnet ID 7200, are currently in operation.
The majority of the spam comes with double-zipped archive attachments.
The mass mailings are using similar distribution methods to previous Locky campaigns, leading the researchers to believe that those behind the activity are ramping up their use of the same sending infrastructure as previously used.
The researchers said they first spotted a spurt in Dridex activity at the end of March. Compared to previous timeframes, the increased activity registered as a comeback in high volume, yet is a small portion of what once was previously seen.
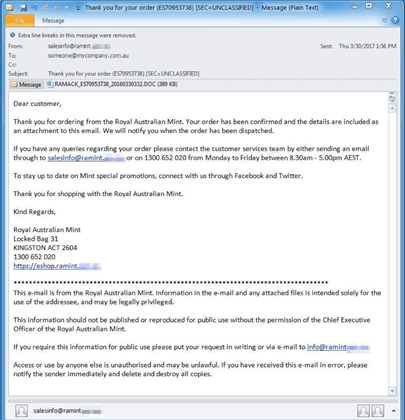
On March 20, the Proofpoint investigators observed the reawakened Dridex activity with botnet ID 7200 being disseminated via Zip- or RAR-compressed VBS and EXE attachments. If executed, the scripts delivered an iteration of the Dridex banking trojan with botnet ID 7200.
The activity is mainly taking place in Australia, France, and the UK.
On March 31, the team again detected a Dridex botnet ID 7200 campaign being distributed via Zip-compressed executables. The subject line in these emails read "payment request" and included a zip attachment posing as an invoice, but which, if clicked, would deliver an executable that downloaded the Dridex banking trojan with botnet ID 7200.
Other messages arrived with MS Word doc attachments that used a macro to download Dridex botnet 7500. Buried inside the first zip file was another zip file, this one containing a Dridex botnet 7500 executable.
This instance of Dridex was observed specifically targeting organisations in Australia, Proofpoint said.
The researchers noted that the present campaign bears similarities to the 2016 mass volume Locky affiliate ID 3 campaign. Notably, the lures employed by the attackers in the emails use similar strategies.
The return of Dridex lead the researchers to surmise that large-scale malware attacks are likely in the next few months.
While admitting that this resurgence in no way equals the mass activity seen in the first half of 2016, the campaign is notable, they said, because it's a stark contrast to what was experienced in the first quarter of 2017.
The researchers said they were also concerned about the different attachments used in the campaign and the similarities to techniques used in previous Locky and Dridex scourges over the past two years.

.png&h=140&w=231&c=1&s=0)

_(20).jpg&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



