The cybercrime ecosystem is just as susceptible to the invisible hand of the market — and to digital disruption — as the rest of the economy, apparently.

Cyber breaches have cost businesses more than $20 billion already in 2021, and that figure is expected to grow to $265 billion within a decade, according to global risk and insurance business Allianz.
However, market forces and more robust responses from national governments are putting pressure on the criminal ecosystem according to separate data from Coveware, which aggregates global ransomware and cyber extortion data.
In a report by Allianz Global Corporate and Speciality (AGCS) called Ransomware Trends: Risk and Resilience, the company quotes research from Accenture suggesting cyber intrusions have already jumped 125 per cent this year with "ransomware and extortion operations top two contributors behind this triple‑digit increase."
AGCS also notes that according to the US Federal Bureau of Investigation (FBI), "There was a 62 per cent increase in ransomware incidents through the first six months of 2021 in the US, which followed a 20 per cent increase in the number of incidents for the whole of 2020 and a 225 per cent increase in ransom demands."
Scott Sayce, Global Head of Cyber at AGCS and the Global Head of the Cyber Center of Competence for AGCS and the Allianz Group, "The number of ransomware attacks may even increase before the situation gets better. As insurers we have to continue to work with our clients using a combination of policy and service improvements to help businesses understand the need to strengthen their controls.”
Sayce however says, “Not all ransomware attacks are targeted. Criminals also deploy wild scattergun approaches to exploit those businesses that aren’t addressing or understanding the vulnerabilities they may have."
Ransomware as a service
The report says the rise of ‘ransomware as a service’ (RaaS) has made it easier for criminals to carry out attacks, and that RaaS groups like REvil and Darkside "sell or rent their hacking tools to those who carry out the attacks and extort victims. They also provide a range of support services, including helplines and ransomware negotiation services."
Subscriptions to such services come remarkably cheap, starting at as little as $40 a month, however, they are proving to be lucrative with REvil, believed to have collected close to $100 million in ransom payments in the first half of this year.
Michael Daum, Senior Cyber Underwriter at AGCS says “Ransomware is run like a business. All the trends we see, such as the significant increase in the number of groups deploying ‘double extortion’ attacks, the surge in supply chain incidents (and even the emergence of ‘triple extortion’) are all just ways in which criminals are seeking to increase their return on investment and their efficiency, optimising their attacks in order to get the best outcome.”
Cryptocurrency is also a significant contributing factor in the rise of ransomware, especially Bitcoin which is believed to account for 98 per cent of ransomware payments during 2019, according to research by Coveware.
Crypto is the cybercrime enabler, allowing criminals to bypass traditional institutions and remain anonymous, according to Thomas Kang, Head of Cyber, Tech and Media, North America at AGCS. "More stringent enforcement and compliance with ‘know‑your‑customer’ and anti‑money laundering laws could, however, help disrupt the ransomware business model."
Invisible Hand
Alas for the criminal class, digital transformation is proving disruptive, as is the determination of the US and other governments to attack the incentive structure of the cybercrime economy.
Coveware says the average size of ransomware payouts is dropping — and apparently, market forces are to blame.
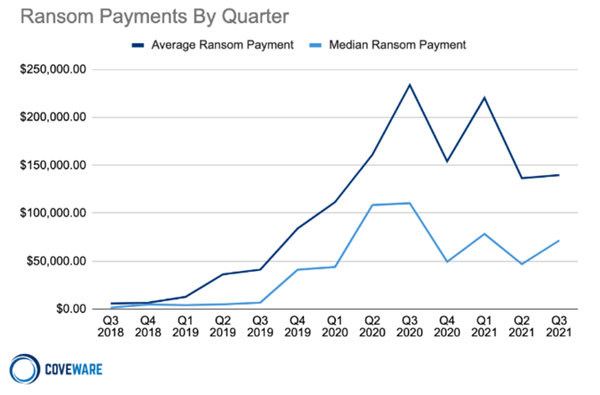
In its Q3 report, Coveware calculated that the average ransom payment to be $139,739 (basically flat on the previous quarter), although the medium payment spiked over 50 per cent to $71674.
It seems market forces are at work. Indeed in its Q2 report Coveware said, "The decrease was primarily driven by a growing number of disparate Ransomware-as-a-Service brands that have proliferated recently, and which have diluted the concentration of attacks controlled by just a few."
"The lower prevalence of several groups that have historically made some of the highest demands (such as Ryuk and Clop) allowed the average and median ransom payment to drift lower during the quarter. Additionally, the efficacy of data exfiltration as an overall tactic appears to also be diminishing. During Q2, over 80 per cent of ransomware attacks also included the threat to leak stolen data."
And it appears the more robust responses of governments around the world — which increasingly treat ransomware as a national security problem — are having an effect.
The Coveware report says, "Ever since the pipeline attacks this spring, we have seen statistical evidence and intelligence showing that ransomware actors are trying to avoid larger targets that may evoke a national political or law enforcement response. This shift from ‘Big Game Hunting’ to ‘Mid Game Hunting’ is personified in both the ransom amount statistics but also the victim size demographics from the quarter. "


.png&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)

_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards







.jpg&h=271&w=480&c=1&s=1)




_(1).jpg&h=140&w=231&c=1&s=0)



