Over a hundred Australian e-commerce sites contain a malicious script that is capable of intercepting users' payment information and exfiltrating it to hackers.
Security researcher Willem de Groot scanned websites running the popular Magento shopping cart software, and found that thousands run the Magentocore.net "skimmer" script that captures form input data.
De Groot said Magentocore.net has been planted on thousands of e-commerce sites using brute-force password guessing to gain access to the Magento administrative control panel.
Scans using the PublicWWW site source code search engine found 105 Magentocore.net infested sites in the .au namespace, and 11 in .nz.
The real number of malware laden sites in Australia could be higher as not all use .au domain names.
The disclosure of the infestation closely follows the release of AusPayNet payments fraud data that showed 87.5 percent of fraud committed against Amex, Visa and Mastercard products (scheme cards) occurs online.
Annual online card losses bloated to a whopping $476 million in the 2017 calendar year, prompting retailers to demand that banks absorb losses rather than just passing them through to merchants.
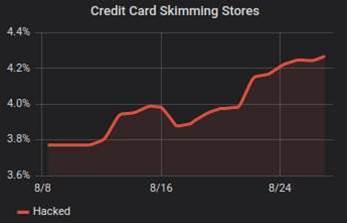
A malware scan of around 220,000 sites by de Groot showed that 4.2 per cent of them were leaking payment and customer data, or 9240 in total that are running one or more malicious scripts.
RiskIQ security researcher Yonathan Klijnsma chimed in on Twitter to say that one of three Magecart groups in Russia that his company has been tracking since 2015 is responsible for the Magentocore infestation.
Among Magecart's more notorious heists is the June 2018 data breach at TicketMaster, which saw details of five per cent of its customers taken.
Site operators not patching their Magento sites have left them open to malicious script injection. De Groot suggested merchants analyse backend logs to indentify how attackers got access to sites, and close the backdoors all at once.
He also advised operators to remove the malware and audit code, and implement better security practices with timely patching, and strong passwords for staff.



.png&h=140&w=231&c=1&s=0)

_(20).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



