Developers of the popular peer to peer BitTorrent file sharing protocol have closed a vulnerability that could have been used to launch large-scale denial of service attacks.

The vulnerability was made public earlier this month by researchers Florian Adamsky, Muttukrishnan Rajaran, Rudolf Jäger and Syed Ali Khayam, who discovered the issue in July.
The flaw meant an attacker sending specially-crafted data packets could generate up to 50 times as much traffic towards targets as originally initiated - 120 times as much in the case of the BT Sync protocol - to potentially swamp victim networks.
SInce the traffic in question would be via the stateless send-and-forget user datagram protocol (UDP), it would be easy for attackers to forge a source address for the data packets and hide their origination.
BitTorrent vice president of communications Christian Averill told iTnews the company's engineering team had been working on ways to mitigate the vulnerability after being alerted to it on July 1.
Averill noted there had been no distributed reflective denial of service (DrDoS) attacks yet using BitTorrent. but said the fact they could be launched meant the issue had to be taken seriously.
BitTorrent software engineer Francisco de la Cruz said the problem lay in a flaw within the libµTP component.
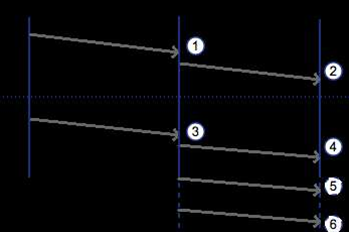
A patch to libµTP, used by BitTorrent, uTorrent and BT Sync, tightens up the conditions under which clients will transition into a connection state for traffic.
Clients will only transition if they receive valid acknowledgement packets from connection initators, and drop those that fail to meet this condition.
This, de la Cruz said, reduced the bandwidth amplification factor (BAF), making attacks very high-effort.
Although it was theoretically possible to abuse BT Sync to generate 120 times traffic amplification, Averill said even before the libµTP patch, there were mitigating factors - such attackers having to know user "secrets", as well as a limit to the amount of peers that shared information with one another.
Combined, these factors meant BT Sync would not be suitable as a source for large-scale denial of service attacks, Averill said.


.png&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



