Amazon Web Services is working to shore up the security of its Simple Storage Service following a string of sensitive information leaks by customers who inadvertently left their data buckets open to the public.
In recent months the likes of Accenture, Dow Jones, Verizon, Viacom and Booz Allen Hamilton have all had highly sensitive data exposed after leaving it unlocked in the AWS cloud storage service.
The issue prompted AWS to issue a warning to its S3 customers in July to make sure their access controls on their buckets were properly configured.
But just last week a researcher discovered 50,000 records belonging to a handful of Australian government agencies and several private sector companies sitting exposed in an S3 bucket.
From today, S3 will now warn users with a prominent indicator if buckets on the storage service are publicly accessible.
Customers can also copy over access control lists and tags associated with objects when replicating data across regions, AWS said today.
This allows the owner of the destination S3 bucket to have full access to the objects being replicated.
Likewise, customers can now choose a destination key when replicating encrypted objects across regions; previously it was not possible to replicate encrypted objects on S3 because the key management service (KMS) credentials were specific to particular AWS regions.
Importantly, customers can now specify that objects in S3 buckets must be stored encrypted, without having to formulate a policy that rejects data at rest in clear text for compliance requirements.
Three options for server-side encryption are also being offered for S3 objects, with the keys for the default encryption managed by either S3, the AWS KMS, or by customers themselves.
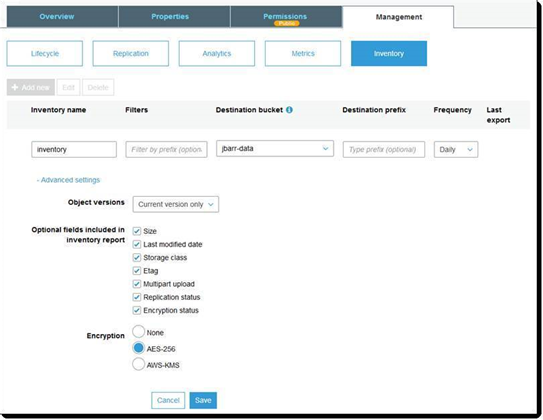
AWS S3 will also provide a detailed inventory report - which can be encrypted - that shows the encryption status of each object in the data bucket.
The new security and encryption options are available for free, and can be enabled via the S3 management console.


_(28).jpg&h=140&w=231&c=1&s=0)


.png&h=140&w=231&c=1&s=0)



_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition












_(1).jpg&h=140&w=231&c=1&s=0)



