Countries like Australia may well wince at exploding online credit card fraud levels, but in the land where credit cards were invented, card sharps are sticking to a tried and tested technology to bypass a massive EMV security crackdown: the humble magnetic stripe.
That's the bleak and rather counter-intuitive picture painted by a new study suggesting that when it comes to fraud, it really doesn't matter how many cards get chipped if merchants still default to vulnerable and increasingly compromised swipe terminals.
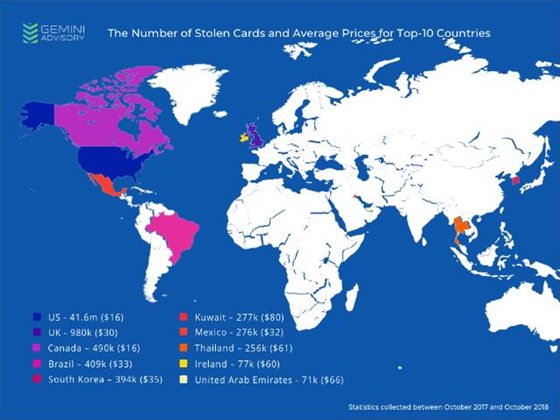
In a paper certain to irritate global card schemes, security vendor Gemini Advisory used what it says is telemetry data collected from illegal web-based market places and found that at least 60 million US cards were compromised in the past year.
It's a big number; so big it infers US efforts to bring merchants along for the EMV ride (think chip and PIN) aren't working anywhere near as well as they should and cultural norms, like signing for a transaction (and adding a tip), just aren't going away.
The Gemini Advisory estimate is also the polar opposite of card fraud in Australia, where CNP fraud on all cards accounts for 85 percent of local card fraud volume at last count.
In the US, three-quarters of compromised cards were likely compromised through skimming card data and point of sale breaches at merchants, Gemini Advisory said.
Put simply, the information recorded on the cards was stolen during transactions - known as Card Present or CP.
The US cards being compromised aren't exactly legacy plastic either.
A staggering nine out of ten records, 41.6 million, stolen during CP transactions were from cards with the EMV security chip, the smartcard functionality of which is arguably only decorative if customers and merchants just continue to swipe, rather than tap or insert, their plastic.
Despite increases stemming from large-scale hacks and breaches of e-commerce databases, there were still far fewer compromised Card Not Present (CNP) records up for sale on the internet, just 14.2 million in the last 12 months.
The Australian comparison is stark.
The last official estimate of skimming and cloning losses across both proprietary debit (eftpos) and scheme cards (Mastercard, Visa and Amex) came in at $47.3 million for 2016 to 2017 compared to $444 million for card not present, a factor just below 10.
Eurovision not materialising
The ambivalence of US banks and retailers to having foreign transaction standards foisted on them is well established. Payments, like aviation, are a geopolitical tussle.
The primary purpose of EMV chips on cards is to enable end-to-end encrypt data during card present transactions and was rolled out across European Union soon after the new millennium to thwart counterfeiting and fraud losses for banks and retailers.
However, the US did not start the migration to EMV until 2015, and services stations won't have to upgrade to secure chip card payments terminals until 2020. Fuel remains one of the biggest purchasing categories in the US.
While most US cardholders have been issued EMV cards, many merchants still haven't upgraded their terminals or PoS software because of the high cost of equipment, Gemini Advisory said.
Merchants often prefer to stick with older terminals and simply ask customers to swipe cards during transactions rather than inserting them. That's understandable if a customer doesn't know their PIN and is used to signing.
But such fallbacks bypass EMV security features, and predictably leaves transactions open to CP fraud.
World leader
The lack of merchant EMV compliance also means the US is the largest source of compromised EMV payments card data for sale on the "dark web", Gemini Advisory said.
Over the past 12 months, just 4.6 million EMV cards from the rest of the world were offered for sale on illegal internet forums, compared to the 41.6 million American ones.
Card data is purloined and exfiltrated from terminals with malware deployed by financially motived threat groups named Fin6 and Fin7 among others, security vendors have found.
A more manual and elaborate method utilised by skimmer groups involves using custom hardware, so called "shimmers", to capture track 1 and 2 data from EMV cards during CP transactions.
The shimmers are inserted into automated teller machines or PoS terminals, and sit between the EMV chip and the reader in the device.
Skimmers can then record track 1 and 2 data from the cards, which can then be onsold to fraudsters who record it onto any magnetic strip.
This technique only works if the issuing bank neglects to check the dynamic Card Verification Value (CVV) during the transaction.
Although the US Payments Forum said EMV technology is cutting CP fraud, physical fraud and the growing volume of CNP data breaches from online merchants remain a strong systemic concern.
In 2017, the Nilson Report tallied up [pdf] US$22.80 billion worth of card fraud worldwide for 2016, a figure the payments industry publication believes could grow by 45 per cent a year and hit US$12 billion by 2020.



_(23).jpg&h=140&w=231&c=1&s=0)







 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



