Researchers have discovered a new variant of the vulnerability in the third version of the SSL (secure sockets layer) web encryption protocol, dubbed POODLE, which has left many different websites open to man-in-the-middle attacks.

Google security engineer Adam Langley noted that while Google, Firefox and others have "done pretty well at killing off SSL version 3" in response to the original POODLE attack by moving to Transport Layer Security (TLS), this alone was not enough to secure websites.
SSL3 uses CBC-mode ciphers that don't specify the contents of CBC padding bytes, opening SSL3 up to an oracle attack. Google and others had removed SSL3 in favour of TLS because TLS specifies the contents of the padding bytes and therefore stops the attack.
But Langley and other researchers today noted that the function used for padding data in TLS is a subset of the same function in SSL3 - meaning attackers could use an SSL3 decoding function with TLS and the POODLE attack would work, Langley wrote.
"This seems a good moment to reiterate that everything less than TLS 1.2 with an authenticated encryption with associated data (AEAD) cipher suite is cryptographically broken," Langley wrote.
The new attack is easier to conduct than the original POODLE exploit, with fewer steps and far fewer transactions required for attackers to guess the content of encrypted payloads.
Testing by security vendor Qualys SSL Labs site showed that attacking web browsers through the flaw required just 256 requests to uncover one cookie character, and 4096 attempts for a 16-character cookie.
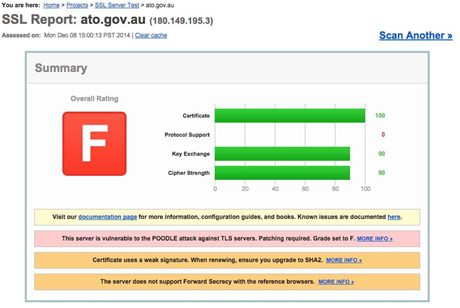
The SSL server test run by Qualys shows that several high profile sites - including the Australian Tax Office and the MyGov portal - are vulnerable to the POODLE attack.
Two of National Australia Bank's servers also test as vulnerable against POODLE, as does the main Westpac website.
iTnews has contacted the ATO, NAB, and Westpac for comment.
A CommBank spokesperson said the bank had patched a vulnerable server overnight after learning of the flaw.
[Update 10/12/14 5:20pm] A spokesperson for the ATO also said the organisation had already addressed the issue.
"The POODLE/TLS vulnerability cannot be used to gain entry into the ATO environment. The ATO was made aware of the vulnerability on 8th December when the initial notice was released and are rectifying it. This work is being treated as high priority," she said.
[Update 11/12/14 2:20pm] A spokesperson for Westpac said: "Westpac is aware of this issue and we take Online Banking security very seriously. We continue to provide up to date security advice to customers through the Security section of our website."
Qualys' director of application security Ivan Ristic said the comparatively low number of requests meant that the new POODLE attack was "quite practical."
Furthermore, he said attackers no longer needed to cause connection failures and force browsers to retry connections to older protocol versions like SSL3 because the exploit exists in TLS 1.2.





_(36).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



