Customers buying goods and services online risk having their credit card details skimmed and transmitted to unknown criminals in Russia through thousands of hacked Magento stores worldwide.

Magento hoster and security specialist Willem de Groot showed iTnews a list of 5900 sites around the world running unpatched, vulnerable versions of the web shopping cart, which have been hacked to serve up malicious Javascript code to unsuspecting customers.
Some 267 vulnerable Australian and New Zealand Magento stores were found by de Groot, who has set up the Magereport site, providing a free check to see if the latest patches are installed for the popular e-commerce platform.
The Australian sites range from online retail shops to art galleries and not-for-profit organisations. iTnews contacted a sample of operators, asking if they were aware of the issue and if they intended to address it.
Most of those contacted did not respond, but Bart Nanka, who manages an online Queensland organic herbs retailer, said the company's development team patched the site after being notified by iTnews of the issue.
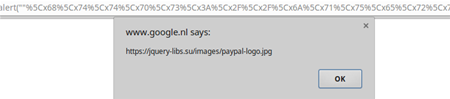
Some Australian sites on de Groot's list are blocked by Google's Safe Browsing feature, used in Chrome and other browsers to warn users of malware.
Analysis by de Groot of the obfuscated malicious Javascript revealed that the code captures credit card details entered by customers and transmits them to a site hosted by a Russian provider.
The card skimming occurs without customer interaction or notification. De Groot said the skimming incidents have been taking place since November 2015, thanks to site operators being slow to patch their stores for Magento vulnerabilities.
One high-profile website that served up the card-skimming Javascript malware is run by the United States Senate Republicans for soliciting donations. The site was patched earlier this month, but de Groot estimated that the malicious Javascript had been injected into its Magento cart some six months ago.
A conservative calculation of visitors to the Republicans site placed the number of stolen cards at 21,000 since March this year. At US$30 per card, the criminals would have made US$600,000 or thereabouts from the Republicans site alone, de Groot said.
The number of e-commerce sites serving up the malicious Javascript to customers has risen sharply since November last year when the malware first appeared.
De Groot counted 3501 vulnerable sites in November 2015, but in September this year, the number was 5925, an increase of 69 percent.
Worldwide, governments, pop stars, car makers, fashion retailers and non-government organisations all run vulnerable sites that are skimming visitors' credit card details, de Groot said.
The malware authors have evolved their code since last year with multi-layer obfuscation to make it harder to detect, and better algorithms to capture payments pages and providers such as Paypal.
De Groot counted at least nine varieties of the malicious Javascript in three distinct families.
He warned that apart from being blocked by Google, sites that serve up the card skimming malware could be penalised by issuers such as MasterCard and Visa.




_(37).jpg&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



