A researcher at security vendor Trellix has uncovered a Linux malware attack that embeds malicious code directly into file names, a technique that bypasses most traditional security defences.
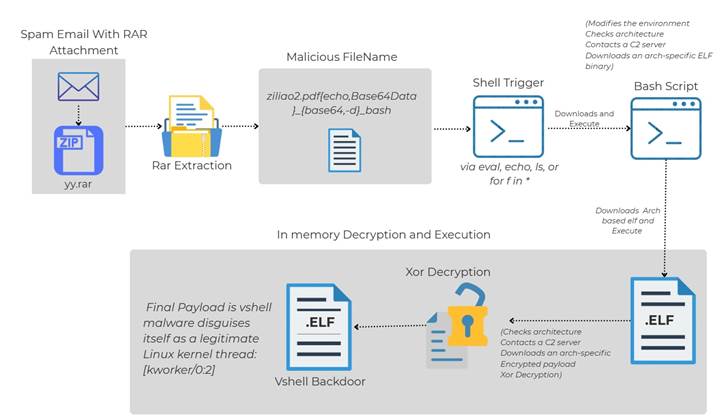
The attack involves crafting a file name that contains bash command interpreter shell code which, if executed, sets in motion a Linux-specific malware infection chain, researcher Sagar Bade wrote.
Unlike traditional malware that is stored as file content, embedding commands into the file name itself makes the malicious code hard to detect, particularly when, as in the sample Trellix discovered, it is Base64 encoded for obfuscation.
Bade said that antivirus engines don’t usually scan file names, and static analysis and behavioural detection tools might not catch such malware either.
None of the commercial anti-malware scanners on Google’s VirusTotal site flagged the file with the malicious code in the 163 character name as malicious in iTNews’ testing.
A spam email with a malicious Roshal Archive (RAR) file was the initial delivery vector, the Trellix researcher said.
Although opening the RAR file doesn’t execute the malware code, the payload can be triggered by any command that expands file names, and processes them.
This could be commands such as eval, echo, printf or logging, Bade said, as the technique abuses that many command shells evaluate or echo filenames without sanitisation.
The researcher identified multiple trigger scenarios beyond simple file listing operations, including backup scripts, audit automation, and system maintenance routines that process files automatically.
When run, the maliciously-named file started a multi-stage infection process, that contacted a command and control (C2) server to download additional scripts, which in turn are used to fetch binary executable for a final payload.
That final payload is the VShell malware which provides threat actors with backdoor access including remote shell access and command execution, file upload, download, and deletion capabilities, process management and control, port forwarding and network tunnelling, and encrypted command-and-control communications.
VShell malware is a Go-language based backdoor used primarily by Chinese advanced persistent threat (APT) groups especially Linux servers.
Trellix found that the malware behaves like "Snowlight", which is a known Linux dropper that automatically runs malicious commands by manipulating files and filenames.
Snowlight has been used to deploy VShell.
Researchers have considered the use of file names to embed commands in the past.
In 2019, researcher John Page documented a technique to inject commands in unsanitised Microsoft PowerShell file names, using Base64 encoded strings.


_(33).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)







 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



