
Cheap home alarms, door opening systems and wireless mains switches can be bypassed with low-cost and homemade devices that can replicate their infrared signals.
Using kit purchased online Canberra-based researcher Silvio Cesare found three ways to bypass a home alarm unit which could be extended to attack other fixed-code radio frequency systems.
"The list of hacking opportunities is pretty big," Cesare said in a blog detailing the research.
The first attack method used a re-purposed remote that replayed the codes within radio signals used to arm and disarm the home alarm system.
Another more simple method used a a $20 "infrared toy" purchased online that could analyse, capture and replay infrared signals to arm and deactivate alarm systems.
"It may take a few goes to capture it, but once captured you can replay it at will. How easy is that?" Cesare said.
But an even more basic method to disarm some alarm systems including the unnamed model tested was to simply purchase another alarm system of the same model and use the included remote. This worked because the vulnerable systems lacked an identifying transmission code.
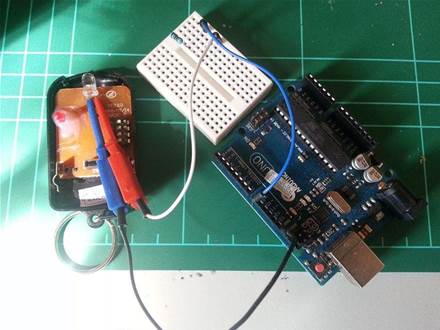
In building the repurposed remote, Cesare cloned the infrared carrier wave to mimic his target alarm system. It required only an Arduino, breadboard and minor electronic components.
The second attack method built a remote using a frequency counter and oscilloscope.
'Learning' remotes which captured radio frequency signals did not work.
The rolling code systems used for keyless entry into some modern cars was not vulnerable to replay attacks.
Cesare said consumers should "remember to buy a decent home alarm system" and avoid cheap options.
He will present the research and further findings at the Melbourne Ruxcon conference in October.


.png&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



