The world was a dangerous place these past five years but no one seemed to notice.
Asian government agencies and high-profile businesses were hacked in massive espionage attacks that point to China, a McAfee investigation has found.
In two attacks, the Olympic Committee of an unnamed Asian nation and a South Korean Government agency failed to notice hacking attacks that had persisted for more than two years.
 |
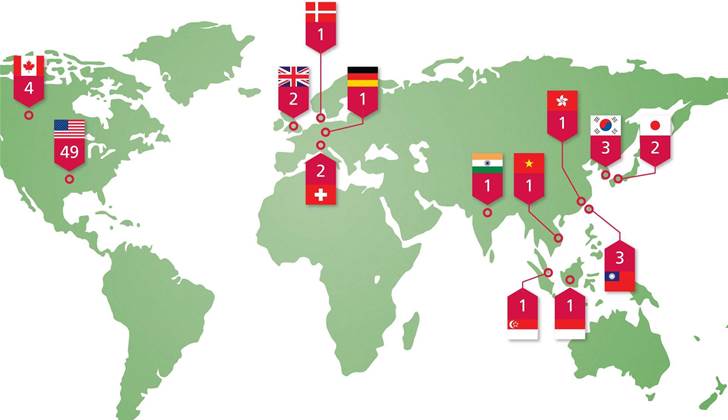
Federal government agencies, defence contractors and electronics companies were some of the organisations in 14 countries that were hacked, McAfee said.
Analysis of the logs uncovered that victims were:
- 22 government agencies
- 13 defence contractors
- 12 communications firms
- 12 non-profit think tanks
- six engineering firms
- four from private industry
- 49 were in the US based
- four in Canada
- two each in Britain, Japan and Switzerland
Dimitri Alperovitch who led Operation Shady RAT said "every company in every conceivable industry with significant size and valuable intellectual property and trade secrets has been compromised or will be shortly".
Alperovitch who was also McAfee vice president of threat research said most victims rarely found an intrusion or understood its its impact and the Fortune Global 2000 was divided into those that know they were compromised and those who don't.
“I have often been asked by our worldwide customers if they should worry about such sophisticated penetrations themselves or if that is a concern only for government agencies, defence contractors and perhaps Google. My answer in almost all cases has been unequivocal: absolutely.”
He said that Advanced Persistent Threats were a "far greater threat to companies and governments, as the adversary is tenaciously persistent in achieving their objectives" but what was witnessed over the "past five to six years has been nothing short of a historically unprecedented transfer of wealth".
The loss of data was also considered, with Alperovitch calling it a "massive economic threat not just to individual companies and industries but to entire countries". He said the public and often industry did not understand the depth of the security threat. And this was due to the few voluntary disclosures by victims of intrusions compared to the number of compromises.
The analysis found that the tactics were established and most victims fixed infections. McAfee detected the malware variants and other relevant indicators with Generic Downloader.x and Generic BackDoor.t heuristic signatures and access to a command-and-control server found a basic entry procedure.
“The compromises themselves were standard procedure for these types of targeted intrusions: a spear-phishing email containing an exploit is sent to an individual with the right level of access at the company and the exploit when opened on an unpatched system will trigger a download of the implant malware,” he said.
“That malware will execute and initiate a backdoor communication channel to the command and control web server and interpret the instructions encoded in the hidden comments embedded in the web page code.
“This will be quickly followed by live intruders jumping on to the infected machine and proceeding to quickly escalate privileges and move laterally within the organisation to establish new persistent footholds via additional compromised machines running implant malware, as well as targeting for quick exfiltration the key data they came for.”
Raj Samani, a chief technology officer at McAfee, said the main point of the attack was that it went on for five years in some cases, despite the few number of victims.
He said he was "not surprised" that victims were slow to realise.
"TK Maxx only knew about the intrusion when the network was running slow," Samani said.
"You can add technologies and keep going but five years is a long time."
A McAfee report and blog analysis was online.











 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



