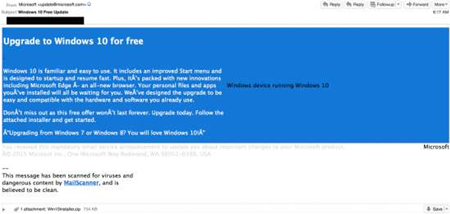
Opportunistic attackers are taking advantage of impatient Windows users by sending out phishing emails designed as a Windows 10 upgrade alert from Microsoft, but which instead delivers ransomware.
Unsuspecting PC owners have begun receiving emails - which appear legitimate - containing a .zip compressed email attachment purporting to be a Windows 10 installer, according to Cisco's security team.
Windows 10 became available in Australia and 189 other countries last Thursday. It is offered as a free download for activated copies of Windows 7 and 8, but the volume of traffic generated by millions of users wanting to upgrade their operating systems is causing delays.
"The fact that users have to virtually wait in line to receive this update makes them even more likely to fall victim to this campaign," Cisco infosec researcher Nick Biasini wrote in a blog post.
He said scammers are spoofing the sender's email address to make it appear as though the email is from Microsoft. The message actually originated from an IP address allocated to a network in Thailand, he said.
Similarly, the attackers have mimicked the blue and white colour scheme used by Microsoft in its Windows 10 branding in the dodgy emails, making them appear more legitimate than run-of-the-mill phishing emails.
Windows 10 scam email. Source: Cisco
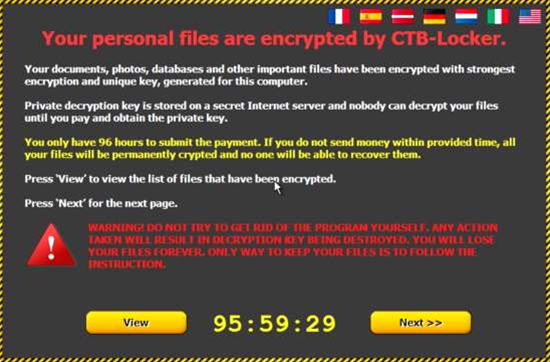
Once a user downloads the attached .zip file, rather than receiving a Windows 10 installer, a piece of ransomware dubbed CTB-Locker launches and encrypts the user's files.
The malware requests payment within 96 hours to decrypt the documents. If users fail to pay within that period of time or attempt to remove the ransomware, the blackmailers threaten to destroy the decryption key and leave files permanently scrambled.
Biasini said the ransomware was being delivered to users at a high rate.
The attackers' use of bitcoin for payment and a command server over the Tor anonymity network for communication made tracing those behind the ransomware emails difficult.
Biasini said CTB-Locker contained several features that differed from large-scale ransomware: CTB-Locker uses elliptical curve encryption rather than RSA asymmetric encryption, and only offered a 96 hour window to pay for file decryption - shorter than standard.
The ransomware is also using hard-coded IP addresses on non-standard ports to communicate, rather than compromised Wordpress sites as other recent versions do.
Additionally, CTB-Locker is exchanging a significant amount of data between systems - around 100 network streams to various IP addresses - which Biasini said was largely uncharacteristic for ransomware.
Cisco advised users to keep an external backup of their files, and pointed out Microsoft was not distributing Windows 10 through emails or attachments. The company has opted to automatically download the OS onto systems of users who previously opted to upgrade.
Windows 10 has been installed on more than 14 million devices since it launched.


_(33).jpg&h=140&w=231&c=1&s=0)








 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



