The United States government chief information office has published a set of technical guidelines that state the administration's many different websites should use the encrypted HTTPS only.

The memorandum - published by US government CIO Tony Scott - requires that "all publicly accessible federal websites and web services only provide service through a secure connection".
"All browsing activity should be considered private and sensitive," Scott wrote.
The standard hypertext transport protocol transmits data in clear text only. This makes users browsing on government websites vulnerable to interception and alteration of data, as well as privacy violations.
Correctly configuring HTTPS with digital certificates is notoriously difficult to do right.
Although both https://cio.gov and https://whitehouse.gov pass muster on the Qualys SSL Labs test - earning an A+ and A rating respectively - iTnews found the sites link to digital certificates with weak security configuration using Secure Hash Algorithm-1 signatures.
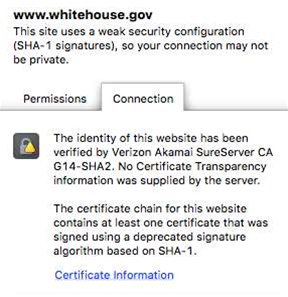
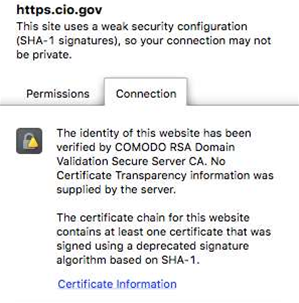
SHA-1 is designed by the US National Security Agency (NSA) and been considered outdated and easy to crack for the last few years.
In 2012, recruitement and job seeker website LinkedIn suffered a large-scale data breach that saw attackers dump almost 6.5 million usernames and passwords, the latter encrypted with SHA-1 and therefore being relatively easy to decrypt.
The order from the White House for US government sites to move to HTTPS-only content serving comes as IT industry giants hit back over the Obama administration's proposed backdoors in encryption for agencies.


_(33).jpg&h=140&w=231&c=1&s=0)


_(36).jpg&h=140&w=231&c=1&s=0)





 Cyber Resilience Summit
Cyber Resilience Summit
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
Huntress + Eftsure Virtual Event -Fighting A New Frontier of Cyber-Fraud: How Leaders Can Work Together
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026












_(1).jpg&h=140&w=231&c=1&s=0)



