The world has been hit by a fresh ransomware epidemic spreading rapidly around the globe that uses the same tools exploited in the recent WannaCry epidemic.
The threat appears to be a variant of the Petya malware, which surfaced last year and crashes computers, rebooting them after rewriting the hard disk master boot record.
Security firm Bitdefender labelled it an "almost identical clone" of the GoldenEye variant of Petya, which emerged last December.
This new GoldenEye variant has two layers of encryption: one that individually encrypts target files on the computer, and another that encrypts NTFS structures, Bitdefender said, preventing victim PCs from being booted up in a live OS environment and retreiving stored information or samples.
Like Petya GoldenEye encrypts the entire hard disk drive and locks users out - unlike Petya, however, there is no workaround for victims to retrieve decryption keys. It also keeps crashing the computer to trigger a reboot until the ransom is paid.
In early analysis other researchers have called the strain spreading today Petya, NotPetya, PetrWrap and Diskcoder.c.
What do we know so far?
The ransomware epidemic appears to have started in Ukraine, where financial documention software company MeDoc was hacked and distributed the malware as an update to customers.
Other reports suggest the ransomware is spreading via emailed attachments and social engineering attempts. Once the malware has infected a system, it tries to replicate itself to other machines on local networks.
The malware writers are using multiple attack vectors to ensure large amounts of infections.
Petya runs legitimate administration tools like Mimikatz to grab user credentials for system access. Once it has obtained the credentials, it passes them onto the Windows PsExec remote administration tool. The malware can also use the Windows Management Instrumentation (WMI) administration feature.
If it succeeds in infecting a system with Domain Administrator rights, the malware can spread to all other systems connected to the machine on a local network.
Security vendor Kaspersky noted that the new GoldenEye variant also uses two modified exploits linked to the NSA, EternalRomance and EternalBlue. The latter was also used by WannaCry.
The exploits target vulnerable computers that run the Windows System Message Block (SMB) version 1 file sharing protocol. Microsoft has issued patches for the vulnerability for both supported and unsupported versions of Windows.
Who is doing this and why?
As of writing, it is not known who is behind the new ransomware campaign.
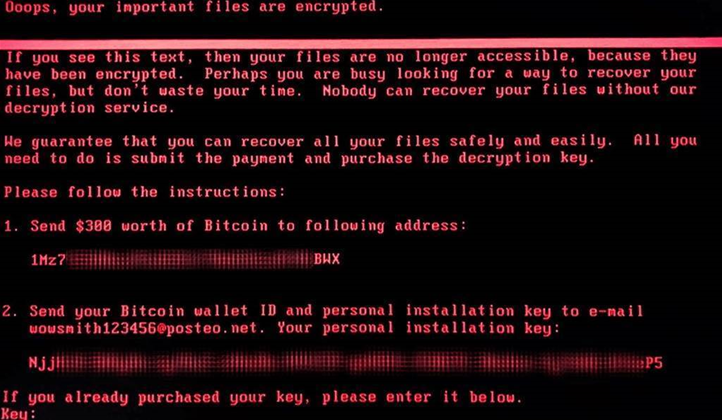
The attackers demand US$300 (A$396) in ransom to release the files.
However, the email address used by the attackers has been blocked, meaning anyone who pays the ransom won't get the decryption keys to unlock their files.
Email provider Posteo said it decided to block the attackers' account once it became aware they were using its service.
What can I do to protect my systems?
Apply patches immediately against the MS17-10 vulnerability, and turn off SMBv1 to limit the attack surface the ransomware exploits.
Ensure that systems with administrative rights are protected with up to date anti-malware, as they can spread the infection to machines that are patched.
I've been hit. How do I recover?
Security researchers advise against paying the ransom because it's unlikely that doing so will result in victims receiving a key to decrypt their scrambled files, given the email address has been blocked.
The good news, however, is that there is a window of opportunity for victims to recover their files before they are scrambled.
The ransomware reboots infected systems to start the encryption of the Master File Table on the hard disk, and inserts a custom Master Boot Record that displays the extortion notice to users.
It takes between ten minutes and an hour after infection to reboot and start the lengthy encryption process - security researchers suggest victims use this time to turn off their computers to halt the encryption process, and to copy over files manually from hard disks.
Creating a perfc.dat file on a local hard drive appears to stop Petya infections via WMI and PsExec, researchers have discovered.
However they warn that this "kill switch" is no substitute for patching systems and protecting them with up to date anti-malware; attackers can easily modify Petya to ignore the perfc.dat file.
#Petya encrypts ON BOOT. If you see CHKDSK message your files not yet encrypted, power off immediately. You can recover with with LiveCD. pic.twitter.com/nKL4Xixjn9
— Hacker Fantastic (@hackerfantastic) June 27, 2017




.png&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



