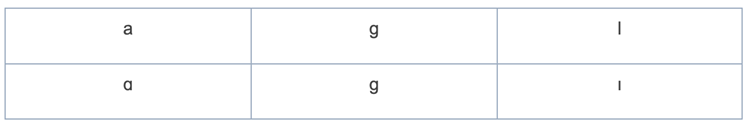
Verisign, which operates the .com and .net registries has deployed changes to its rules to prevent registration of bogus, lookalike domain names using Unicode International Phonetic Alphabet Extension characters that appear visually similar to standard letters such as a, g and i, but are treated differently by computer systems.
Security vendor researcher Matt Hamilton successfully registered a bucket with a cloud provider, with a Unicode emoji character in November 2019.
He was curious if it was possible to register Unicode Latin IPA homoglyphs in bucket names and sub-domains, which it was.
"I then checked if it was possible to register domains with these homoglyph characters. Ruh-roh, it was," Hamilton said.
Hamilton then spent approximately US$400 on registering a bundle of 17 .com domains, using International Phonetic Alphabet Extension homoglyphs to demonstrate the vulnerability.
He was able to register domain names that look deceptively similar to well-known internet brands and properties, such as amazon.com, apple.com, gmail.com, netflix,com, theguardian.com and more.
Of the three homoglyphs, the ɡ voiced velar stop is the most convincing character that is nearly indistinguishable from its Latin letter counterpart, Hamilton said.
The Latin Alpha homoglyph is also very convincing, especially when not adjacent to the standard Latin a letter.
Another lookalike character, the Latin Iota, is the least convincing of the three and on some systems and fonts looks similar to a lower-case L and not like the Latin i letter.
The researcher has promised to transfer the homoglyph domain registrations to the owners of the non-homographic equivalents at no cost.
Verisign acknowledged the issue and thanked Hamilton for bringing it to the company's attention.
"While the underlying issue described by Mr Hamilton is well understood by the global Internet community – and is the subject of active policy development by ICANN [the Internet Corporation for Assigned Names and Numbers] – we appreciate him providing additional timely details about how this issue may be exploited," Verisign said.
"Although we understand that ICANN has been on a path to address these issues globally, we have also proactively updated our systems and obtained the necessary approval from ICANN to implement the changes to the .com and .net top-level domains required to prevent the specific types of confusable homograph registrations detailed in Mr. Hamilton’s report," the gTLD operator aded.
Homograph and homoglyph attacks is a known problem, allowing malicious users to for example replace the Latin a character with the Cyrillic a, to create resource locators that look deceptively similar to legitimate ones.
Verisign has been aware of the issue, and implemented anti-homograph measures such as disallowing mixed scripts for domain registrations.
Hamilton discovered that it was possible to bypass Verisign's registration rules if the lookalike Unicode characters were Latin IPA Extension ones.
Apart from Verisign, Amazon Web Services S3 has remediated the vulnerability, by preventing registrations that start with the "xn--" Punycode that is used for Unicode characters.
Hamilton also reported the vulnerability to Google, cloud storage company Wasabi, DigitalOcean and notified them in February that the issue had been reclassified as a zero-day after finding fake HTTPS certificates and an unofficial Javascript library hosted on an unnamed but prominent domain, using homograph lookalike characters.
There was no response from the above infrastructure as a service providers however.
While Google prevents creation of buckets that contain "google" or close misspellings such as "g00gle" in the name, Hamilton said it is possible to register ones that use Unicode Latin IPA Extension homoglyphs.
He also contacted the United States Computer Emergency Response Team (US CERT) about the vulnerability but did not get a response from them.
Hamilton believes the vulnerability has been abused for the past three years,
"Between 2017 and today, more than a dozen homograph domains have had active HTTPS certificates," Hamilton said.
"This included prominent financial, internet shopping, technology, and other Fortune 100 sites."
"There is no legitimate or non-fraudulent justification for this activity," he added.


.png&h=140&w=231&c=1&s=0)
_(33).jpg&h=140&w=231&c=1&s=0)

_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



