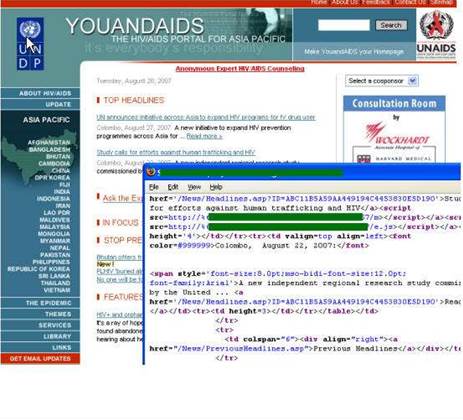
The method scans for multiple un-patched Microsoft vulnerabilities in an aim to install a back-door Trojan, according to Joel Camissar managing director A/NZ at Websense.
“Rather than looking for one exploit – which is the norm - it looks for several and hones in on one to then install a Trojan horse,” said Camissar.
“When the Web site is visited, a malicious JavaScript file (e.js) is executed. Site visitors infected with this malicious code will have a Trojan downloaded and backdoor installed on their desktops,” according to a Websense advisory.
First discovered on 17th August, the technique was used to attack a prominent Indian bank and a US biotechnology company, said Camissar.
“And this campaign is hosted by the same group,” he added.




_(23).jpg&h=140&w=231&c=1&s=0)
_(36).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



