An German government-commissioned security analysis of the popular free disk encryption program TrueCrypt has found that it is safe from exploitation in most circumstances, contradicting earlier suggestions it should no longer be used.
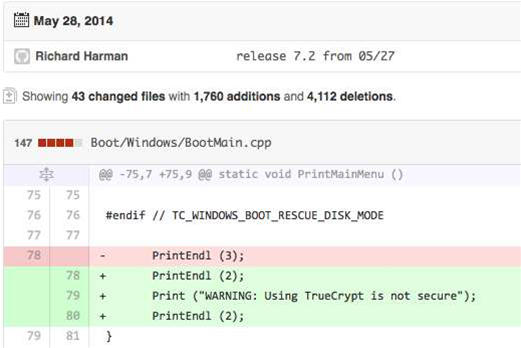
The open source tool, developed anonymously, has been scrutinised by researchers since May last year when a remark in its code warned against the use of TrueCrypt.
TrueCrypt is used by millions of people, and Amazon Web Services, to encrypt sensitive data.
In a detailed technical analysis [pdf] of the source code of the last released version (7.1a) the researchers noted that while the application of cryptography in the tool is not optimal, they found no evidence "that the guaranteed encryption characteristics are not fulfilled in the implementation of TrueCrypt".
As TrueCrypt is a software-only solution, it can only provide protection when an encrypted disk is lost, stolen or in a deactivated, or unmounted, state.
"TrueCrypt does not provide any protection against active attack scenarios such as the installation of a key logger or malware. To protect against these would require hardware-based security measures such as those provided by a TPM or smartcard," the researchers wrote.
However a number of new weaknesses in TrueCrypt were discovered by the researchers too.
The Linux random number generator implementation in TrueCrypt needs improvement, the researchers noted.
Weak random number generation makes it easier for attackers to guess the keys used to decrypt scrambled data.
Together with the Open Crypto Audit Project, the researchers found that the implementation of the Windows random number generator in TrueCrypt is potentially dangerous.
Other problems found in TrueCrypt were a non-timing-resistant implementation of the Advanced Encryption Standard (AES), key files not being used in a cryptographically secure way, and data volume headers not being properly protected.
Overall however, the flaws in TrueCrypt are relatively minor and hard for attackers to exploit, the researchers believe.
TrueCrypt's lack of documentation for the code and overall system architecture makes maintenance and updates of the tool by third parties difficult, the researchers said.
From the user perspective, TrueCrypt comes with a detailed handbook which unfortunately is poorly structured making information hard to find. Much of the information requires in-depth technical knowledge.
The TrueCrypt analysis was done by the Fraunhofer Institutue for Secure Information Technology in Darmstadt, on behelf of Germany's Bundesamt für Sicherheit in der Informationstechnik (BSI) or Federal Office for Information Security.


_(33).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)

_(28).jpg&h=140&w=231&c=1&s=0)





 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



