Google's move to blacklist from its iconic search an entire Second Level Domain (SLD) considered to host a stockpile of malicious sites "doesn't make sense", according to a security researcher.

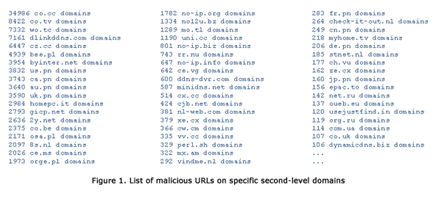
The co.cc domain was offered for free by a Korean company with the same name, and was identified by the Anti-Phishing Working Group in April to have been a launching pad for 5000 phishing attacks, with the lion's share occuring in the first half of last year (pdf).
"Subdomains are often registered by the thousands at one time and are used to distribute malware and fake anti-virus products on the web. In some cases our malware scanners have found more than 50,000 malware domains from a single bulk provider," said Google's a
"To help protect users we recently modified those systems to identify bulk subdomain services which are being abused. In some severe cases our systems may now flag the whole bulk domain."
But Google's move to censor the domain is ineffective, according to IT security company TrendLabs.
"Based on our research and monitoring of malicious domains and cybercrime activity, we know for a fact that all major cybercriminals have already moved from .co.cc to other similarly abused second-level domains like .rr.nu or .co.tv," said TrendLabs research director Martin Roesler.
“…the malicious SLDs are more often used for the second, third, up to the fourth jumps or redirections. The doorway pages – the pages that are actually indexed by search engines – very rarely use .co.cc. So blocking them makes no sense.”
The problem Roesler said is that SLDs are used only briefly to elude detection and maintain the viability of blackhat search engine optimisation schemes.
For example, the .tk domain, based in Tokelau, was rated as one of the worst in the world for harbouring registered malcious sites by the same April report that flagged the notorious co.cc domain. All but about 100 of the 2500 attacks that originated from the .tk domain were from registered websites.
More complex
Bu the problem was expected to get even more complex with the revamp of Top Level Domains (TLD) allowing a near limitless abundance of domains, making Google’s blacklisting efforts unviable, while efforts to block malware alone had already failed.
Roesler said Google should instead use its weight to force registrars to pull the plug on SLDs housing malicious sites.
“This is much more effective instead of simply restricting user access to an entire block since we know cybercriminals will just choose to jump SLDs [and] this also unjustifiably penalises those who are actually using the said SLD for legitimate purposes.”

_(33).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)






 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



